All Mail Brute 2025
Email account breaches remain one of the most damaging and prevalent threats in cybersecurity, serving as gateways to corporate espionage, financial fraud, and identity theft. Automated credential-cracking tools have become increasingly sophisticated, evolving to bypass modern security measures, such as multi-factor authentication (MFA) and account lockout policies. The 2025 generation of these attack platforms demonstrates alarming advancements in adaptive brute-force techniques, enabling attackers to compromise email accounts at scale systematically. These tools are particularly dangerous because they automate what was once a manual process, allowing even unskilled threat actors to launch devastating attacks against individuals and organizations alike.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
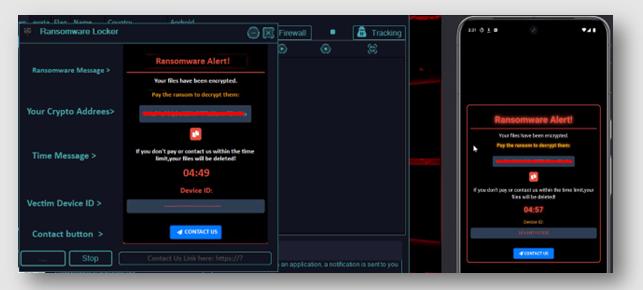
All Mail Brute 2025 software is an advanced email account cracking tool designed to automate large-scale credential attacks against various email providers and corporate mail systems. It combines sophisticated password-guessing algorithms with evasion techniques to bypass security protections while maintaining a low detection profile. Cybercriminals typically use it for credential stuffing attacks, corporate espionage, and as the initial access vector for more complex attacks, such as business email compromise (BEC). The toolkit’s effectiveness stems from its ability to adapt to various email protocols, security challenges, and defensive mechanisms while operating undetected by most security monitoring systems.
Key Features of All Mail Brute 2025
| Feature | Description |
| Protocol Support | Works with SMTP, IMAP, POP3, Exchange, and OWA |
| Adaptive Engine | Automatically adjusts attack patterns based on target responses |
| Proxy Integration | Supports rotating proxy chains and Tor networks |
| MFA Bypass | Includes techniques for circumventing some multi-factor authentication |
| Dictionary Builder | Generates targeted wordlists based on victim information |
| Success Analyzer | Identifies and verifies compromised accounts automatically |
| Stealth Mode | Mimics legitimate user behavior to avoid detection |
How All Mail Brute 2025 Works
The attack process follows a carefully orchestrated sequence designed to maximize success while minimizing detection:
Target Acquisition & Reconnaissance
- Ingests target lists from various sources (data breaches, phishing campaigns)
- Performs email provider fingerprinting to determine protocol and security settings
- Gathers intelligence about password policies and lockout thresholds
- Builds customized attack profiles for each target domain
Credential Generation
- Creates targeted password candidates using:
- Known password dictionaries
- Rules-based mutations (capitalization, l33t speak, appending numbers)
- Previously breached credentials
- Victim-specific information (names, birthdays, company terms)
- Organizes attempts to appear as legitimate login patterns
Adaptive Attack Execution
- Distributes attempts across multiple IPs and time intervals
- Dynamically adjusts based on target responses:
- Slows down when encountering rate limits
- Changes the protocols if blocked
- Switches to alternative authentication methods
- Implements session persistence techniques to maintain access
Post-Compromise Actions
- Automatically verifies successful logins
- Performs mailbox reconnaissance (identifying valuable data)
- Sets up mail forwarding rules for persistent access
- Exports credentials and session tokens for later use


