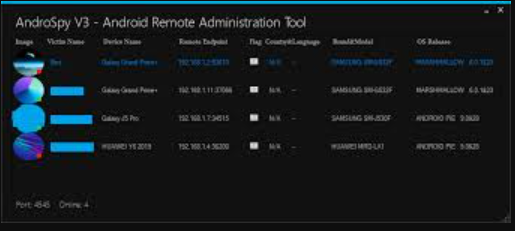
AndroSpy-v3
The mobile threat landscape has grown increasingly sophisticated, with AndroSpy v3 emerging as a particularly dangerous tool in modern cyberattacks targeting Android devices. This advanced surveillance malware exemplifies how cybercriminals are developing more stealthy and feature-rich tools to compromise smartphones. This malware has been actively used in targeted attacks against individuals and organizations, demonstrating its effectiveness in bypassing mobile security measures. Its ability to harvest sensitive data while remaining undetected makes it a significant threat in an era where mobile devices store critical personal and professional information.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What is the AndroSpy v3
This software is a sophisticated Android surveillance tool designed to covertly monitor and exfiltrate a wide range of sensitive data from infected devices. Functioning as a powerful spyware package, it targets call logs, messages, location data, and device usage patterns. The malware is typically distributed through malicious apps masquerading as useful utilities, productivity tools, or entertainment applications on third-party app stores. Once installed, it operates silently in the background, collecting extensive personal data while employing various techniques to avoid detection and removal. Its modular design allows attackers to customize the feature set based on their surveillance objectives.
Key Features
| Feature | Description |
| Call Monitoring | Records incoming/outgoing calls and captures contact lists |
| Message Interception | Collects SMS, MMS, and messaging app communications |
| Location Tracking | Provides real-time GPS positioning and movement history |
| Media Exfiltration | Steals photos, videos, and audio recordings from device storage |
| Keylogging | Captures keystrokes and input across applications |
| Screen Recording | Takes periodic screenshots and records device activity |
| App Usage Monitoring | Tracks which applications are used and for how long |
| Remote Control | Allows attackers to execute commands on infected devices |
| Self-Protection | Uses obfuscation and anti-removal techniques to maintain persistence |
How the AndroSpy v3 Works
The malware employs a multi-stage infection process and sophisticated data collection methodology:
1. Delivery and Installation
Initial infection typically occurs through:
- Trojanized applications.
- Social engineering attacks.
- Exploit kits.
The installation process:
- Requests extensive permissions (contacts, microphone, location, etc.).
- Disguises its presence using generic app names and icons.
- May delay malicious activity to bypass initial security checks.
2. Data Collection Mechanisms
Once active, the malware implements various surveillance techniques:
Communication Monitoring:
- Intercepts calls and messages through Android accessibility services.
- Bypasses encryption in some messaging apps via screen capture.
- Logs communication metadata (timestamps, participants, durations).
Location Tracking:
- Uses GPS, Wi-Fi, and cell tower triangulation.
- Stores and transmits location history at configurable intervals.
- Can activate location services if disabled by the user.
Media Harvesting:
- Scans device storage for specific file types.
- Compresses and encrypts data before exfiltration.
- Monitors new media additions for immediate capture.
3. Data Exfiltration
Collected information is transmitted to attacker-controlled servers via:
- Encrypted HTTPS connections blended with normal traffic.
- Fallback methods using SMS or email when the internet is unavailable.
- Scheduled transmissions during device charging to avoid detection.
4. Persistence and Evasion
The malware employs multiple techniques to maintain access:
- Device administrator privileges.
- Dynamic code loading.
- Process injection.
- Regular updates.
Download Link 1
Download Link 2
Download Link 3
Download Link 4


