ANUBIS 7.0 ANDROID BOTNET (Panel + Builder+ Tutorial)
The rise of mobile-focused malware has introduced dangerous new threats to personal and enterprise security, with advanced botnet frameworks posing one of the most severe risks. Modern Android botnet kits now offer sophisticated infection vectors, evasion techniques, and monetization capabilities that rival traditional Windows malware. ANUBIS 7.0 ANDROID BOTNET toolkits typically include builder applications, command-and-control (C2) panels, and detailed tutorials, lowering the barrier to entry for aspiring cybercriminals while enabling advanced threat actors to conduct large-scale mobile device compromises. The 2024 versions demonstrate particular sophistication in their ability to bypass Google Play Protect, exploit zero-day vulnerabilities, and maintain persistence through system updates.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
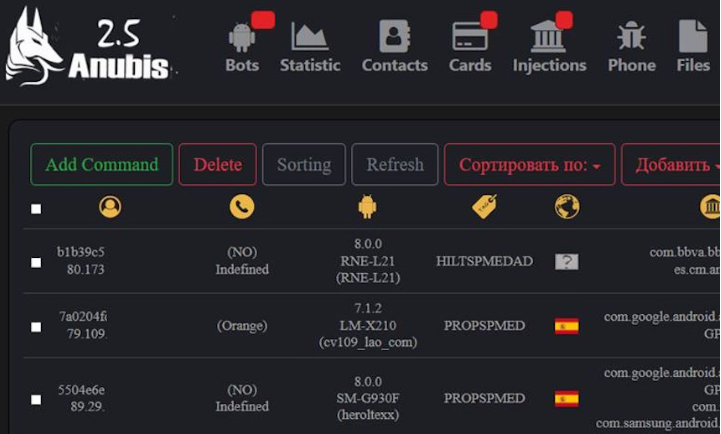
This type of malware toolkit represents a complete ecosystem for creating, deploying, and managing compromised Android devices. The package typically includes three core components: a builder application that generates customized malicious APKs, an administrative panel for controlling infected devices, and documentation explaining deployment strategies. Attackers use these frameworks to create networks of hijacked smartphones and tablets that can be weaponized for various malicious purposes including credential theft, DDoS attacks, click fraud, and cryptocurrency mining. The latest versions incorporate modular plugin architectures, allowing operators to add new functionality to already-infected devices without requiring re-infection.

Key Features
| Feature | Description |
| Polymorphic Payload Generation | Creates unique APK variants to evade signature-based detection |
| Zero-Click Infection | Exploits Android framework vulnerabilities requiring no user interaction |
| C2 Obfuscation | Uses legitimate cloud services as proxy servers for bot communications |
| Dynamic Code Loading | Downloads additional malicious modules after initial infection |
| Anti-Analysis Techniques | Detects and disables security tools/sandboxes on compromised devices |
| Multi-Vector Persistence | Maintains access through notifications, accessibility services, and device admin rights |
| Automated Monetization | Integrates modules for banking fraud, premium SMS abuse, and ad-click bots |
| Geo-Fencing | Activates different payloads based on victim location |
How ANUBIS 7.0 ANDROID BOTNET Works
The botnet operates through a sophisticated infection chain and command structure:
- Payload Creation
- Builder tool configures malicious APK with customized package name, icons, and permissions
- Embeds exploit code targeting specific Android versions or device manufacturers
- Obfuscates critical components using commercial packers or custom encryption
- Distribution Channels
- Third-party app stores masquerading as legitimate software markets
- Social engineering via SMS/phishing linking to drive-by download pages
- Trojanized versions of popular apps distributed through file-sharing sites
- Initial Compromise
- Exploits Android Binder or Intent handling vulnerabilities for privilege escalation
- Gains persistent access by abusing notification listeners or accessibility services
- Registers device administrator privileges to prevent uninstallation


