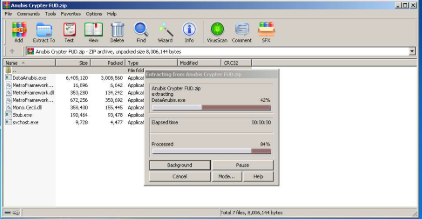
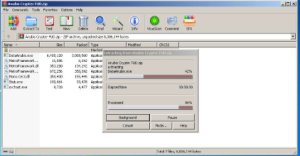
Anubis Crypter FUD 2025
In the arms race between cybercriminals and security professionals, Anubis Crypter FUD 2025 have emerged as a critical weapon for evading detection. The latest iterations of these tools employ increasingly sophisticated methods to bypass even advanced security solutions, enabling malware to operate undetected for extended periods. These evasion capabilities make crypters particularly dangerous in ransomware attacks, corporate espionage, and large-scale credential theft campaigns. As security vendors enhance their detection mechanisms, crypters continue to evolve, incorporating novel techniques to remain fully undetectable (FUD) against modern antivirus, endpoint detection and response (EDR) systems, and sandbox environments.
This software represents a cutting-edge crypter designed to transform recognizable malware into completely undetectable payloads. It utilizes multiple layers of obfuscation and advanced anti-analysis techniques to protect malicious code from security scanners. Primarily used by cybercriminals, it serves as a delivery mechanism for banking trojans, spyware, and ransomware payloads. The software’s effectiveness lies in its ability to dynamically adapt its evasion strategies based on the target environment, making it particularly challenging for automated security systems to detect. While malicious actors predominantly use it, some penetration testers employ similar tools for legitimate security assessments.
Key Features of Anubis Crypter FUD 2025
| Feature | Description |
| FUD Guarantee | Ensures payloads remain undetectable by all major AV/EDR solutions |
| Environmental Awareness | Dynamically adjusts behavior based on detected security measures |
| Memory-Only Execution | Executes payloads without writing files to disk |
| API Obfuscation | Masks system calls to evade behavioral analysis |
| Polymorphic Engine | Generates unique variants for each infection |
| Self-Destruct Mechanism | Automatically removes traces after execution |
How Anubis Crypter FUD 2025 Works
The crypter employs a multi-phase approach to ensure successful payload delivery while maintaining stealth:
- Payload Preparation Phase
- The original malware undergoes multiple transformation stages:
- First-layer encryption using AES-256 with a dynamic key
- Second-layer obfuscation through custom byte manipulation
- PE header reconstruction to eliminate identifiable patterns
- The processed payload is embedded into a specially crafted loader
- Environmental Assessment Phase
Before execution, the loader performs comprehensive system checks:
- Security product detection (AV/EDR process scanning)
- Virtual environment identification (VM artifacts, sandbox indicators)
- User privilege analysis (checks for admin rights)
Based on findings, it selects the optimal execution path
- Stealth Execution Phase
The payload delivery occurs through sophisticated methods:
- Memory Mapping Technique: Allocates executable memory regions and loads payload via reflective loading
- Process Ghosting: Creates temporary process images that self-delete before execution
- Thread Hijacking: Injects code into existing legitimate threads
The execution chain is designed to leave minimal forensic evidence
- Post-Execution Phase
After successful payload deployment:
- The loader activates its self-cleaning routine
- Overwrites memory artefacts and temporary files
- Modifies timestamps to blend with regular system activity
- May deploy false flags to misdirect forensic investigations