Apolon Loader Telegram WEB panel 2023
In recent years, cybercriminals have increasingly relied on sophisticated malware-as-a-service (MaaS) tools to distribute malicious payloads efficiently. One such tool, a Telegram-based web panel Apolon Loader Telegram, has gained notoriety for its ability to bypass security measures and deliver various types of malware. This loader is particularly dangerous due to its user-friendly interface, modular design, and integration with encrypted messaging platforms, making it a preferred choice for attackers targeting businesses and individuals alike.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
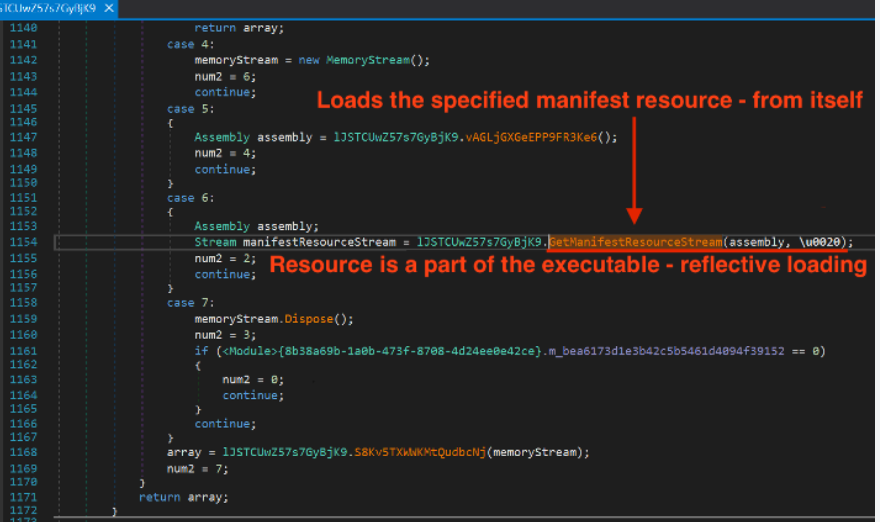
This loader is a type of malicious software designed to retrieve and deploy secondary payloads, such as stealers, ransomware, or remote access trojans (RATs), onto compromised systems. It operates as part of a broader cyberattack chain, often distributed through phishing emails, malicious ads, or fake software downloads. Once installed, it communicates with a command-and-control (C2) server via Telegram’s API, allowing attackers to manage infections remotely through a web-based dashboard.
 Key Features of Apolon Loader Telegram
Key Features of Apolon Loader Telegram
| Feature | Description |
| Telegram C2 Integration | Uses Telegram’s API for stealthy command execution and data exfiltration. |
| Payload Delivery | Dynamically fetches and executes additional malware from remote servers. |
| Persistence Mechanisms | Establishes auto-start registry entries or scheduled tasks to maintain access. |
| Anti-Analysis | Detects virtual machines (VMs) and debugging tools to evade detection. |
| Modular Architecture | Supports plugins for extended functionality, such as keylogging and screen capture. |
| Encrypted Communication | Obfuscates C2 traffic to avoid network-based detection. |
How the Apolon Loader Telegram Works
Infection and Execution
- The loader typically infiltrates a system through social engineering or the use of exploit kits. Once executed, it performs several checks to avoid analysis environments, such as sandboxes or virtual machines.
- If the coast is clear, it establishes persistence by modifying system settings or creating malicious scheduled tasks.
Command-and-Control Communication of Apolon Loader Telegram
- Instead of traditional HTTP-based C2 servers, this loader leverages Telegram’s messaging platform for communication.
- Attackers send commands via Telegram bots, which the malware interprets to perform actions like downloading additional payloads, stealing data, or executing scripts.
- This method provides anonymity and bypasses network-based security controls that may flag suspicious domains or IP addresses.


