ATM Card Cloning All Tools 2025
Cybercriminals continually refine their methods to exploit financial systems, with ATM Card cloning remaining a significant threat. Attackers now utilize highly sophisticated tools to steal card data, bypass security measures, and withdraw funds illegally. These tools employ advanced techniques, including skimming, magnetic stripe manipulation, and malware deployment, which create significant risks for banks and individuals. To develop strong countermeasures, experts must understand how these tools operate.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
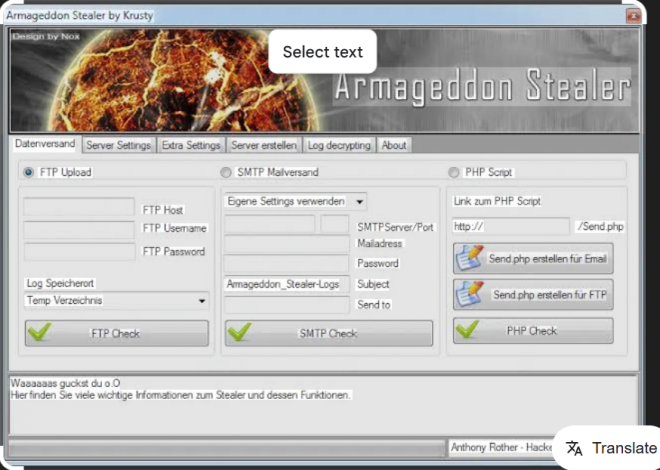
This malicious software enables fraud by capturing, replicating, and manipulating card data. Criminals often combine it with physical skimmers or malware-infected ATMs. The software processes stolen information encodes it onto blank cards, and can even mimic real transactions to avoid detection. While primarily used for illegal activities, cybersecurity researchers also study these tools to enhance fraud prevention systems.
Key Features of ATM Card Cloning Tools
| Feature | Description |
|---|---|
| Magnetic Stripe Data Extraction | Reads and stores data from a card’s magnetic stripe. |
| EMV Chip Bypass | Exploits weaknesses to bypass chip-and-PIN security. |
| Card Data Encoding | Writes stolen data onto blank cards for fraudulent transactions. |
| Skimming Integration | Works with skimming devices to collect card details. |
| Transaction Spoofing | Mimics legitimate transactions to evade detection. |
| Remote Payload Delivery | Deploys malware to ATMs or POS systems via network attacks. |
How ATM Card Cloning Operates
The process involves multiple stages, blending physical and digital techniques to commit fraud.
1. Data Capture
Skimming: Criminals install skimming devices on ATMs or POS terminals to collect magnetic stripe data when victims insert their cards.
Malware-Based Collection: If attackers compromise an ATM with malware, the malicious software logs card details and PIN entries directly from the machine.
2. Data Processing
The software extracts Track 1 & 2 data, which includes card numbers, expiration dates, and authentication details.
If EMV chip data is intercepted, attackers may force transactions to use the weaker magnetic stripe or exploit encryption flaws.
3. Card Cloning
Criminals use a card writer to transfer stolen data onto blank magnetic stripe cards.
Some advanced tools attempt to forge chip data, though EMV security makes this difficult.
4. Payload Delivery (Optional)
If the software supports remote attacks, criminals may infect ATMs through network exploits or USB devices.
The malware can disable security features, alter transaction logs, or trigger unauthorized cash dispensing.
5. Execution
Criminals use cloned cards at ATMs or POS terminals, often in rapid, coordinated attacks to maximize withdrawals before detection.
Some tools spoof transactions to appear legitimate, delaying fraud alerts.