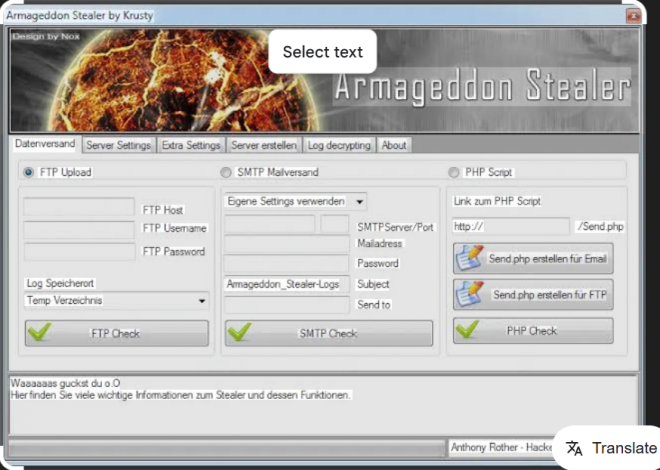
Beaver SMS Bomber 2025
In the evolving landscape of cyber threats, tools designed to disrupt communication systems have become a growing concern. Among these, SMS bombing software has gained notoriety for its ability to overwhelm targets with a flood of text messages, causing service disruptions, psychological distress, and even financial losses. Beaver SMS Bomber 2025 is often exploited in harassment campaigns, social engineering attacks, or as a distraction to mask more sophisticated breaches. While its use is illegal in many jurisdictions, the accessibility and ease of deployment of Beaver SMS Bomber 2025 make it a persistent threat in modern cyber warfare.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
The software in question is an automated tool designed to send a high volume of SMS messages to a target phone number in a short period. Typically, it exploits vulnerabilities in online SMS gateways, APIs, or third-party services to route messages without direct access to the telecommunication infrastructure. While some users may claim it is for “testing” or “pranking,” its primary misuse involves harassment, denial-of-service (DoS) attacks on phone numbers, and social engineering schemes.
Key Features of Beaver SMS Bomber 2025
| Feature | Description |
| Multi-Gateway Support | Utilizes multiple SMS gateways to bypass rate limits and increase message volume. |
| Proxy Integration | Route traffic through proxies to hide the attacker’s IP and evade detection. |
| Custom Message Crafting | Allows attackers to send predefined or randomized text content. |
| Scheduling Capabilities | Enables delayed or timed attacks for coordinated disruptions. |
| API Abuse | Leverages vulnerable or poorly secured APIs to send messages at scale. |
How Beaver SMS Bomber 2025 Works
Techniques and Functionality of Beaver SMS Bomber 2025
The software automates the process of sending SMS messages through various online platforms that offer free or paid SMS services. Instead of relying on a single provider, it distributes the load across multiple gateways to avoid triggering anti-flooding mechanisms. Below is a breakdown of its workflow:
Target Input – The attacker specifies the victim’s phone number, message content, and the duration of the attack.
Gateway Selection – The tool cycles through a list of SMS gateways (often scraped from public sources or purchased) to distribute the message load.
Proxy Rotation – To prevent IP-based blocking, the software routes requests through proxy servers, making detection more difficult.
Message Delivery – The tool mimics legitimate API requests to these gateways, tricking them into processing the messages. Some variants randomize sender IDs or use burner email accounts to register for temporary access to SMS services.