BIG EXPLOIT COLLECTION 2025
In the ever-evolving landscape of cyber threats, BIG EXPLOIT COLLECTION 2025 frameworks have become a favored weapon for both sophisticated threat actors and script kiddies alike. These Swiss Army knife-like toolkits dramatically lower the barrier to entry for cybercriminals by packaging hundreds of weaponized vulnerabilities with automated exploitation capabilities. The 2025 generation of these frameworks represents a significant evolution, incorporating AI-assisted attack chaining, built-in evasion techniques, and cloud-based C2 infrastructure, making them particularly effective against both enterprise networks and individual targets. Their modular nature allows attackers to mix and match exploits based on the target environment while maintaining a low detection footprint.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
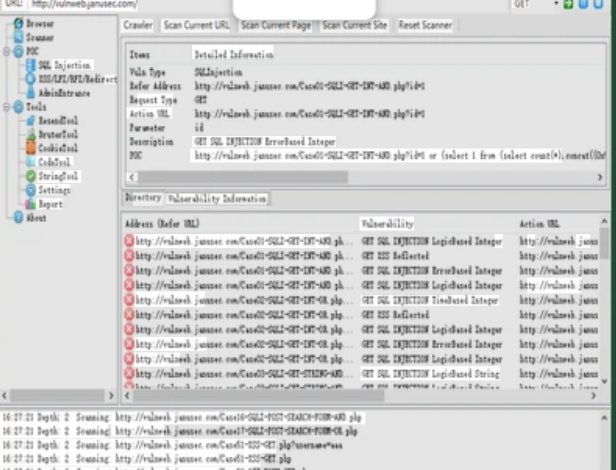
This software is a massive, regularly updated collection of exploits and attack tools packaged into a single unified platform. It functions as an all-in-one offensive security solution containing over 500 verified exploits spanning two decades of vulnerabilities, from legacy system weaknesses to freshly discovered zero-days. The framework is typically used for penetration testing, but its leaked and cracked versions have been widely adopted by cybercriminals for network breaches, ransomware deployment, and creating botnets. What makes it particularly dangerous is its self-updating mechanism, which pulls new exploit modules from underground repositories, ensuring that attackers always have fresh attack vectors at their disposal.

Key Features
| Feature | Description |
| Vulnerability Database | 500+ pre-loaded exploits with search/filter capabilities |
| Auto-Exploit | AI-assisted vulnerability matching and attack chaining |
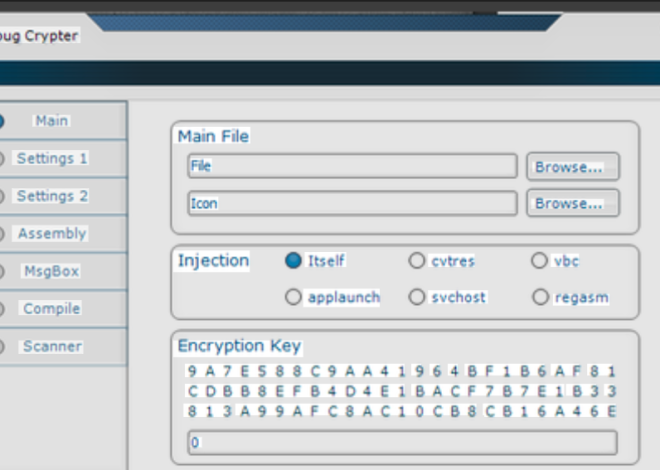
| Payload Factory | Generates undetectable malware for multiple platforms |
| C2 Integration | Built-in connections to major botnet frameworks |
| Evasion Toolkit | Automated obfuscation and anti-sandbox techniques |
| Lateral Movement | Privilege escalation and network propagation modules |
| Zero-Day Feed | Subscription-based access to unpublished exploits |
How a BIG EXPLOIT COLLECTION Works
The framework operates through an intelligent, multi-phase attack process:
- Reconnaissance & Fingerprinting
- Conducts automated network scanning using adaptive techniques
- Performs comprehensive OS/service fingerprinting
- Matches discovered systems against its vulnerability database
- Generates an attack tree with multiple potential exploitation paths
- Exploit Selection & Customization
- Recommends optimal exploits based on target characteristics
- Automatically customizes shellcode to bypass security controls
- Generates target-specific payloads using polymorphic techniques
- Implements necessary evasion measures for the environment
- Execution & Compromise
- Deploys exploits using the most effective method:
- Remote Code Execution: For network-accessible services
- Client-Side Attacks: Weaponized documents/links for users
- Physical Device Exploits: For IoT and peripheral devices
- Establishes multiple redundant footholds
- Deploys persistence mechanisms appropriate to the system
- Post-Exploitation Automation
- Performs automated privilege escalation
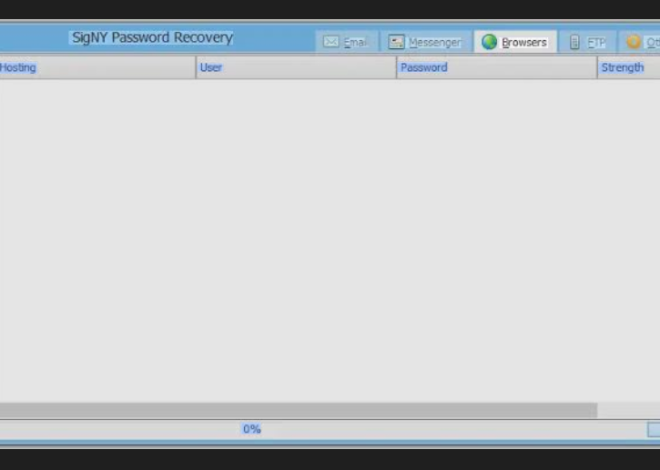
- Conducts credential harvesting from memory and disks
- Map nthe etwork topology for lateral movement
- Deploys secondary payloads (ransomware, spyware, etc.)