BitRAT HVNC RAT 2025 Cracked with Source code
In the evolving landscape of cyber threats, remote access trojans (RATS) remain a persistent and dangerous tool for attackers. These malicious programs enable unauthorized access to compromised systems, allowing cybercriminals to steal sensitive data, deploy additional malware, or maintain long-term persistence within a network. Among these threats, advanced RATS with features like Hidden Virtual Network Computing (HVNC) pose significant risks due to their stealth and ability to evade detection. BitRAT HVNC RAT 2025 iteration of such malware demonstrates increased sophistication, leveraging modern evasion techniques to bypass security measures and remain undetected while exfiltrating critical information.
Download Link 1
Download Link 2
Download Link 3
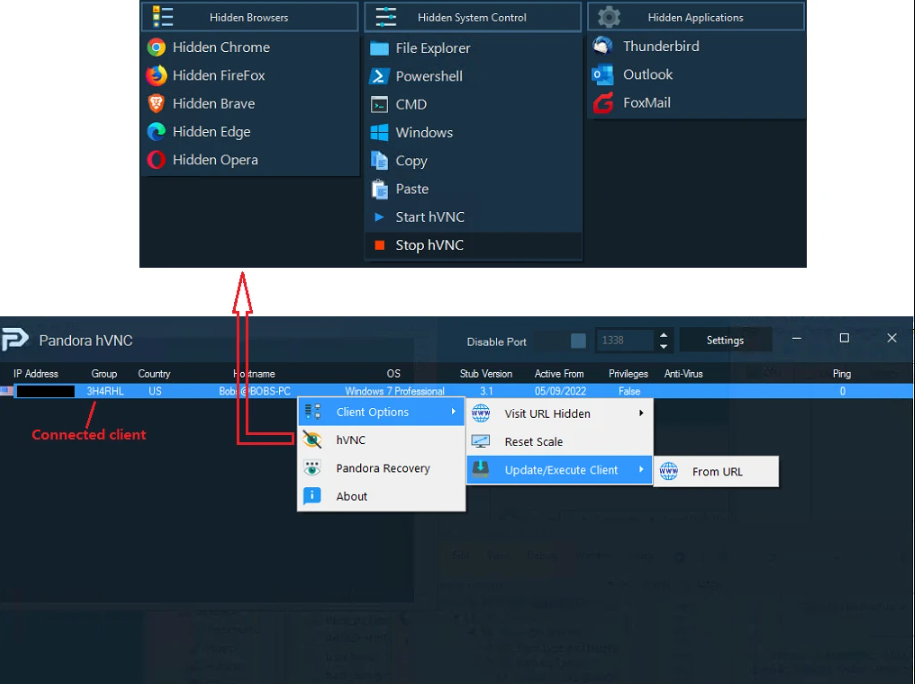
This software is a type of remote access tool (RAT) designed to provide attackers with covert remote control over infected systems. Typically distributed through phishing emails, malicious downloads, or exploit kits, it operates silently in the background, enabling threat actors to execute commands, harvest credentials, and manipulate the victim’s machine without their knowledge. Its HVNC capability allows attackers to interact with the system discreetly, avoiding detection by running sessions in a hidden virtual network connection (HVNC).

Key Features
| Feature | Description |
| Hidden Virtual Network Computing (HVNC) | Operates in a concealed desktop environment, masking remote interactions. |
| Credential Theft | Harvests saved passwords, browser data, and authentication tokens. |
| Persistence Mechanisms | Establishes long-term access via registry modifications or scheduled tasks. |
| Keylogging | Logs keystrokes to capture sensitive input such as login credentials. |
| File Exfiltration | Steals and uploads files from the infected system to the attacker’s controlled servers. |
| Remote Shell Access | Provides command-line control over the compromised machine. |
| Anti-Detection Techniques | Uses obfuscation, process injection, and encryption to evade security tools. |
How BitRAT HVNC RAT 2025 Works
Infection and Delivery
The malware typically infiltrates systems through social engineering tactics, such as phishing emails with malicious attachments or links to compromised websites. Alternatively, it may exploit software vulnerabilities to deliver its payload. Once executed, it establishes persistence by modifying system settings or creating scheduled tasks to ensure it runs after reboots.
Stealth and Evasion
To avoid detection, the malware employs several techniques:
- Process Injection: It injects its code into legitimate system processes, making it harder for security software to identify malicious activity.
- Encrypted Communication: Data exchanged with the attacker’s command-and-control (C2) server is encrypted to bypass network monitoring.
- HVNC Session Concealment: Remote interactions occur in a hidden virtual desktop, preventing the victim from noticing unauthorized access.
Functionality and Payload Execution
Once active, the malware performs reconnaissance to gather system information, such as installed software, network configurations, and user privileges. Attackers then use the RAT’s features to:
- Exfiltrate Data: Sensitive files, credentials, and clipboard contents are uploaded to the C2 server.
- Execute Remote Commands: Attackers can run scripts, manipulate files, or deploy additional malware.
- Maintain Persistence: The malware ensures it remains operational even after system restarts or security scans.


