bitrat HVNC RAT 2025 Cracked with Source code
The underground cybercrime ecosystem continues to evolve with increasingly sophisticated tools becoming available to malicious actors. Among these, BitRAT HVNC RAT 2025 represents a particularly alarming development, combining advanced remote access capabilities with cutting-edge evasion techniques. This malware variant stands out due to its inclusion of Hidden Virtual Network Computing (HVNC) functionality, allowing attackers to operate compromised systems invisibly while bypassing traditional security measures. The availability of both cracked versions and source code has significantly lowered the barrier to entry, enabling less skilled criminals to customize and deploy this powerful threat. Its emergence coincides with a rise in sophisticated credential theft, corporate espionage, and ransomware precursor attacks, making it a favored tool in targeted campaigns against both individuals and organizations.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
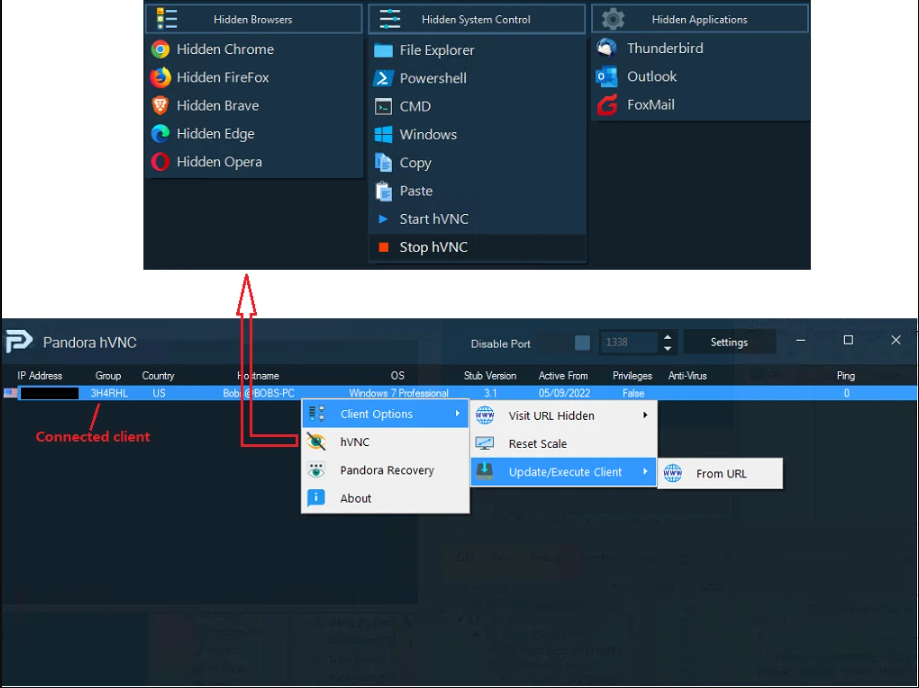
This software is a feature-rich Remote Access Trojan (RAT) designed to provide attackers with complete, covert control over infected systems. The inclusion of HVNC technology allows the malware to establish hidden remote sessions that evade both user awareness and security software detection. Typically distributed through phishing campaigns, malicious downloads, or exploit kits, the RAT specializes in long-term persistence and data exfiltration. Cybercriminals primarily use it for credential harvesting, financial fraud, and as a foothold for deploying secondary payloads like ransomware. The cracked version’s availability has led to widespread abuse, while the included source code enables attackers to modify the malware’s behavior, creating unique variants that bypass signature-based detection.

Key Features
| Feature | Description |
| HVNC (Hidden VNC) | Establishes invisible remote desktop sessions |
| Process Injection | Executes malicious code within legitimate processes |
| Credential Harvesting | Steals passwords from browsers, email clients, and VPN software |
| Keylogging | Logs keystrokes with application context |
| Screen Capture | Records or streams desktop activity |
| Persistence | Maintains access via registry modifications and service installation |
| File Manager | Uploads, downloads, or executes files remotely |
| Cryptocurrency Theft | Targets wallet files and clipboard contents |
| Anti-Analysis | Detects and evades sandboxes and security tools |
How bitrat HVNC RAT 2025 Works
- Infection & Initial Compromise
The malware employs multiple delivery vectors:
- Phishing Emails: Malicious attachments disguised as invoices or documents
- Drive-by Downloads: Exploiting browser vulnerabilities via compromised websites
- Trojanized Software: Bundled with pirated applications or fake cracks
- RDP Brute-Force: Targeting weakly secured remote desktop connections
- Installation & Evasion
Upon execution, the malware performs several critical steps:
- Environment Checks:
- Detects virtual machines, sandboxes, and analysis tools
- Identifies security software processes (AV, EDR)
- Persistence Mechanisms:
- Creates registry entries in HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Installs as a Windows service with a legitimate-sounding name
- Sets up scheduled tasks for periodic reactivation
- Process Hollowing:
- Injects malicious code into trusted processes (e.g., explorer.exe)
- Uses reflective DLL injection to avoid writing to disk
- HVNC Functionality
The malware’s most dangerous capability involves establishing hidden remote sessions:
- Creates a virtual desktop invisible to the user
- Operates in this hidden environment to execute commands
- Bypasses traditional remote desktop detection methods
- Evades screen-locking mechanisms during active sessions
- Data Exfiltration & Attack Modules
Once established, the RAT activates multiple malicious functions:
Credential Harvesting
- Extracts saved passwords from:
- Web browsers (Chrome, Firefox, Edge)
- Email clients (Outlook, Thunderbird)
- FTP and database management tools
- Collects authentication tokens for session hijacking
Financial Data Theft
- Targets cryptocurrency wallet files (Electrum, Exodus, MetaMask)
- Monitors clipboard for cryptocurrency addresses
- Scans for banking credentials in documents and password managers
Surveillance Capabilities
- Activates webcam and microphone for ambient recording
- Captures screenshots at configurable intervals
- Logs keystrokes with window titles for context
- Command & Control Communication
The malware employs sophisticated C2 infrastructure:
- Primary Channel: Encrypted WebSocket connections
- Fallback Methods: DNS tunneling or Telegram bot API
- Data Obfuscation: Compresses and encrypts stolen data before exfiltration
- Modular Updates: Downloads additional payloads as needed


