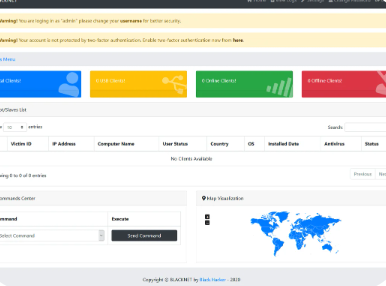
BlackNET 3.0 Panel with Builder
BlackNET 3.0 Panel with Builder is a sophisticated, yet controversial, remote administration tool (RAT) that has gained notoriety in cybersecurity circles. Designed with both a user-friendly control panel and a customizable builder, this tool enables remote system management but is often exploited for malicious purposes. While it has legitimate uses for IT administration, its potential for abuse makes it a significant concern for cybersecurity professionals.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What Is BlackNET 3.0 Panel with Builder?
BlackNET 3.0 is a Windows-based RAT that provides attackers with extensive control over compromised systems. The included Builder tool allows customization of the RAT’s payload, enabling threat actors to evade detection and tailor attacks to specific targets. Unlike legitimate remote management tools, BlackNET is frequently distributed through underground forums and used for unauthorized access, data theft, and other cybercriminal activities.
Detailed Features
- User-Friendly Control Panel: Intuitive dashboard for managing infected systems.
- Custom Payload Builder: Generates unique RAT executables with configurable settings.
- Persistent Access: Maintains long-term control via registry edits or task scheduling.
- Keylogging: Captures keystrokes to steal sensitive information.
- Screen Capture: Takes screenshots of the victim’s desktop.
- Webcam and Microphone Control: Enables unauthorized audio/video recording.
- File Management: Upload, download, or delete files on the victim’s system.
- Process Manipulation: Terminate or spawn processes remotely.
- Password Recovery: Extracts saved credentials from browsers and applications.
- Anti-Detection Techniques: Obfuscation and encryption to bypass antivirus software.
- Encrypted C2 Communication: Secures traffic between the RAT and the attacker’s server.
- Spread via USB: Optional module to propagate via removable drives.
Why Is It Used?
BlackNET 3.0 is primarily exploited by cybercriminals for:
- Data Theft: Harvesting login credentials, financial information, and personal files.
- Espionage: Monitoring victims through webcams and microphones.
- Botnet Recruitment: Enlisting compromised devices into larger attack networks.
- Ransomware Deployment: Serving as a delivery mechanism for additional malware.
Security Implications and Mitigation
- Detection: Use endpoint detection and response (EDR) tools to identify suspicious behavior.
- Prevention: Educate users on phishing tactics, enforce strong passwords, and disable unnecessary remote access features.
- Legal Consequences: Unauthorized use of tools like BlackNET violates cybersecurity laws globally.
- Ethical Alternatives: Legitimate remote administration tools (e.g., TeamViewer, AnyDesk) should be used for authorized purposes.


