Blank Grabber 2025
Cyber threats continue to evolve, with attackers leveraging increasingly sophisticated tools to exploit vulnerabilities. One such tool, often referred to as “Blank Grabber 2025,” has gained notoriety for its ability to harvest sensitive data from compromised systems stealthily. This malware exemplifies the growing trend of credential theft and information-gathering attacks, which are often used as a precursor to larger-scale breaches, financial fraud, or ransomware deployments. Its modular design and evasion techniques make it particularly dangerous, allowing attackers to bypass traditional security measures while exfiltrating critical data.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software is a type of information-stealing malware designed to extract credentials, session cookies, and other sensitive data from infected machines. It typically targets web browsers, cryptocurrency wallets, and installed applications, collecting login details, autofill data, and even screenshots of user activity. Attackers often distribute it through phishing emails, malicious downloads, or disguised as legitimate software. Once deployed, it operates silently in the background, sending stolen data to a remote server controlled by the attacker. Its primary uses include identity theft, financial fraud, and facilitating further attacks by providing adversaries with access to compromised accounts.
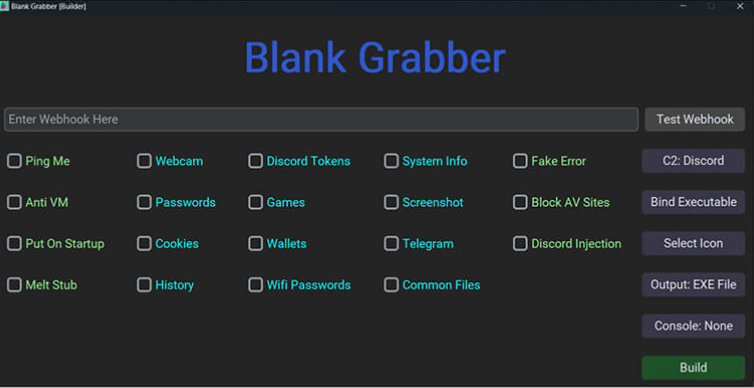
Key Features of Blank Grabber 2025
| Feature | Description |
| Credential Harvesting | Extracts saved passwords and login details from browsers and applications. |
| Session Cookie Theft | Captures active session cookies to hijack authenticated sessions. |
| Screen Capture | Takes screenshots of the victim’s desktop to monitor activity. |
| Keylogging | Records keystrokes to capture typed credentials and messages. |
| Anti-Detection Mechanisms | Uses obfuscation, process injection, and sandbox evasion to avoid detection. |
| Data Exfiltration | Encrypts and sends stolen data to a command-and-control (C2) server. |
| Persistence | Establishes autostart mechanisms to remain active after system reboots. |
How Blank Grabber 2025 Works
Infection and Execution
The malware is typically delivered through social engineering tactics, such as phishing emails with malicious attachments or fake software installers. Once executed, it may employ process hollowing or DLL injection to run within a legitimate system process, making detection more difficult. Some variants also use droppers—a lightweight initial payload—to download and install the full malware suite.
Data Collection Techniques
After gaining a foothold, the malware scans the system for target applications, including web browsers, email clients, and cryptocurrency wallets. It accesses browser databases (e.g., SQLite files storing login credentials) and decrypts stored passwords using built-in decryption routines. For session hijacking, it extracts cookies, allowing attackers to bypass multi-factor authentication (MFA) if sessions are still active. Additionally, keylogging and screen-capture modules may be activated to gather further intelligence.
Evasion and Persistence
To avoid detection, the malware employs techniques such as:
- Code obfuscation to hinder static analysis.
- Process injection to blend in with legitimate applications.
- Sandbox detection to delay execution in virtualized environments.
For persistence, it may modify registry keys, create scheduled tasks, or install itself as a service, ensuring it remains active even after a system restart.


