BTC Clipper 2025
BTC Clipper 2025 has emerged as one of the most insidious financial malware threats in recent years, specifically targeting cryptocurrency users through sophisticated clipboard hijacking techniques. This advanced malware variant represents a significant evolution from earlier crypto-stealing trojans, now incorporating AI-driven behavioral analysis and adaptive evasion mechanisms. Security analysts have observed its deployment across multiple platforms, with particular success against Windows and Android users conducting cryptocurrency transactions. The 2025 version demonstrates alarming improvements in target selection and stealth capabilities, enabling attackers to steal digital assets while bypassing many traditional security measures. Its growing prevalence in dark web markets suggests this threat will continue to evolve and expand throughout the current year.
Download Link 1
Download Link 2
Download Link 3

What is the BTC Clipper 2025
This specialized financial malware operates as a clipboard hijacker designed to intercept and modify cryptocurrency transactions in real-time. The software typically spreads through:
- Trojanized cryptocurrency applications (fake wallets, trading tools).
- Compromised browser extensions for popular crypto services.
- Malicious advertisements on blockchain-related websites.
- Phishing campaigns impersonating crypto exchanges.
Once installed, it enables attackers to:
- Monitor clipboard activity for cryptocurrency addresses.
- Replace legitimate wallet addresses with attacker-controlled ones.
- Bypass basic transaction verification methods.
- Track successful thefts through encrypted logs.
- Adapt to user behavior to avoid detection.
Key Features
| Feature | Description |
| Real-time Clipboard Monitoring | Constantly scans for cryptocurrency address patterns |
| Dynamic Address Substitution | Swaps legitimate wallet addresses with attacker-controlled ones |
| Transaction Context Analysis | Understands when users are preparing transactions |
| Multi-Currency Support | Targets Bitcoin, Ethereum, and other major cryptocurrencies |
| Process Injection | Operates within legitimate processes to avoid detection |
| Self-Destruct Mechanism | Removes evidence when detecting analysis environments |
| Encrypted C2 Communication | Uses secure channels to receive updated target lists |
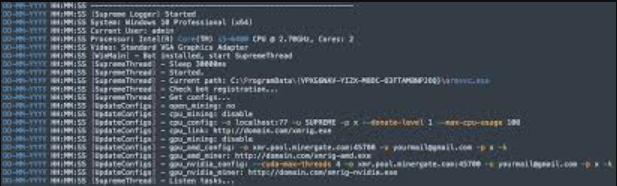
How the BTC Clipper works
1. Infection and Persistence
The malware employs multiple infection vectors:
- Drive-by downloads from compromised crypto websites.
- Trojanized software bundles (disguised as wallet managers).
- Social engineering (fake security updates).
Upon execution, it:
- Establishes persistence through registry modifications or system services.
- Injects into processes commonly used for crypto transactions.
- Downloads current target lists and configuration from C2 servers.
- Begins monitoring system activity for crypto-related operations.
2. Core Hijacking Functionality
The malware operates through a sophisticated multi-stage process:
Detection Phase:
- Uses pattern recognition to identify cryptocurrency addresses.
- Analyzes application context (wallet software, exchange websites).
- Determines transaction values and timing.
Substitution Phase:
- Selects most appropriate attacker address from database
- Maintains address format/length to avoid suspicion.
- For large transactions, use freshly generated addresses.
Verification Phase:
- Confirms address replacement success.
- Logs transaction details for attacker review.
- Adjusts behavior based on success rates.
3. Advanced Evasion Techniques
BTC Clipper 2025 employs several innovative anti-detection methods:
Behavioral Adaptation:
- Learns user transaction patterns before activating.
- Varies attack timing based on victim behavior.
- Avoids modifying small “test” transactions.
Forensic Countermeasures:
- Memory-only operation when possible.
- Encrypted local activity logs.
- Automatic removal when detecting analysis tools.
Network Obfuscation:
- Uses legitimate cloud services for C2 communication.
- Implements blockchain-based fallback channels.
- Rotates infrastructure frequently.


