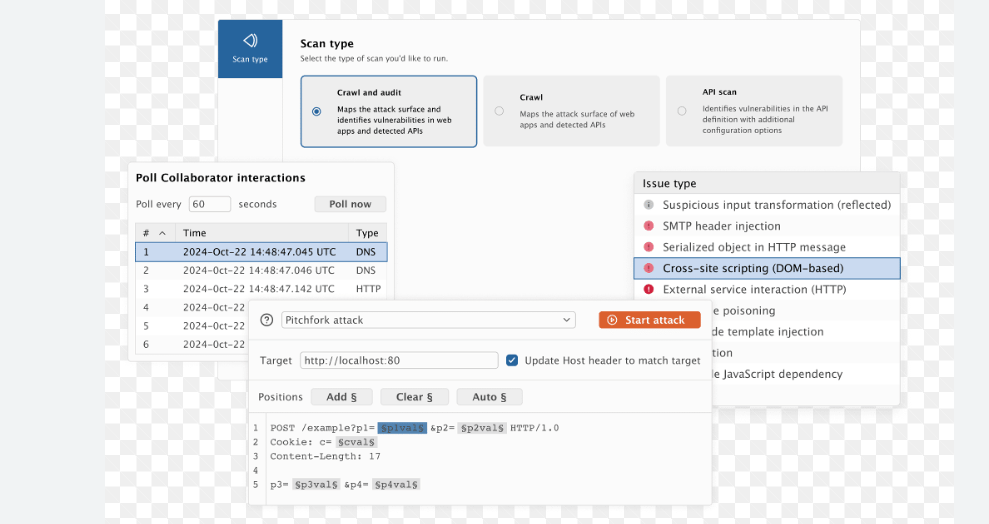
Burp Suite Professional 2021.9 Build 10295
In modern cybersecurity, penetration testing and vulnerability assessment tools play a critical role in both offensive and defensive operations. One such tool, Burp Suite Professional 2021.9 Build 10295, has become a staple for security professionals and malicious actors alike due to its powerful capabilities in web application testing. While ethical hackers use it to identify and remediate vulnerabilities, attackers leverage its features to exploit weaknesses in web applications, intercept communications, and deliver malicious payloads. Its prevalence in cyberattacks highlights the dual-use nature of such tools, where functionality designed for security testing can be repurposed for exploitation.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software is a comprehensive platform for web security testing, primarily used to analyze, attack, and exploit web applications. It functions as an intercepting proxy, allowing users to inspect and modify HTTP/S traffic between a browser and a target server. Every day, use cases include vulnerability scanning, session hijacking, API testing, and brute-force attacks. Security teams rely on it to uncover flaws such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms, while attackers exploit these same vulnerabilities to compromise systems.
Key Features
| Feature | Description |
| Intercepting Proxy | Captures and modifies HTTP/S requests in real time. |
| Web Vulnerability Scanner | Automates the detection of security flaws in web apps. |
| Intruder | Performs customized automated attacks (e.g., brute force, fuzzing). |
| Repeater | Manually manipulates and resends individual requests for testing. |
| Sequencer | Analyses session token randomness to assess entropy. |
| Decoder | Encodes and decodes data (e.g., Base64, URL, HTML). |
| Extensibility | Supports plugins (BApps) for expanded functionality. |
How the Burp Suite Professional 2021.9 Works
The tool operates by acting as a man-in-the-middle (MITM) proxy between the user’s browser and the target web application. When configured, all traffic passes through the proxy, allowing for the inspection and modification of requests and responses. Key techniques include:
- Traffic Interception – The proxy captures HTTP/S requests, allowing users to view headers, parameters, and payloads before forwarding them to the server. This is useful for manipulating input fields or injecting malicious code.
- Active and Passive Scanning – The scanner passively analyzes traffic for vulnerabilities (e.g., exposed sensitive data) or actively probes the application with crafted inputs to trigger flaws like XSS or SQLi.
- Automated Attacks (Intruder) – The Intruder tool automates attacks by iterating through payloads (e.g., wordlists for brute-forcing login credentials or fuzzing for input validation bypasses).
- Session Handling – The tool manages cookies and tokens, enabling session hijacking or replay attacks by reusing authenticated sessions.
![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)