Bruter
Here are all types of bruter like Password Bruters, Hash Bruters, Wi-Fi Bruters, API/Token Bruters, ZIP/RAR Bruters, Credential Stuffing Tools.
Proxy Grabber and Proxy Checker 2025
In the ever-evolving landscape of cybercrime, tools that facilitate anonymity and bypass security measures have become increasingly valuable to threat actors. Among these, proxy manipulation utilities have gained prominence as they enable attackers to mask their activities and evade detection. The 2025 versions of Proxy Grabber demonstrate sophisticated capabilities that go beyond simple proxy management, […]
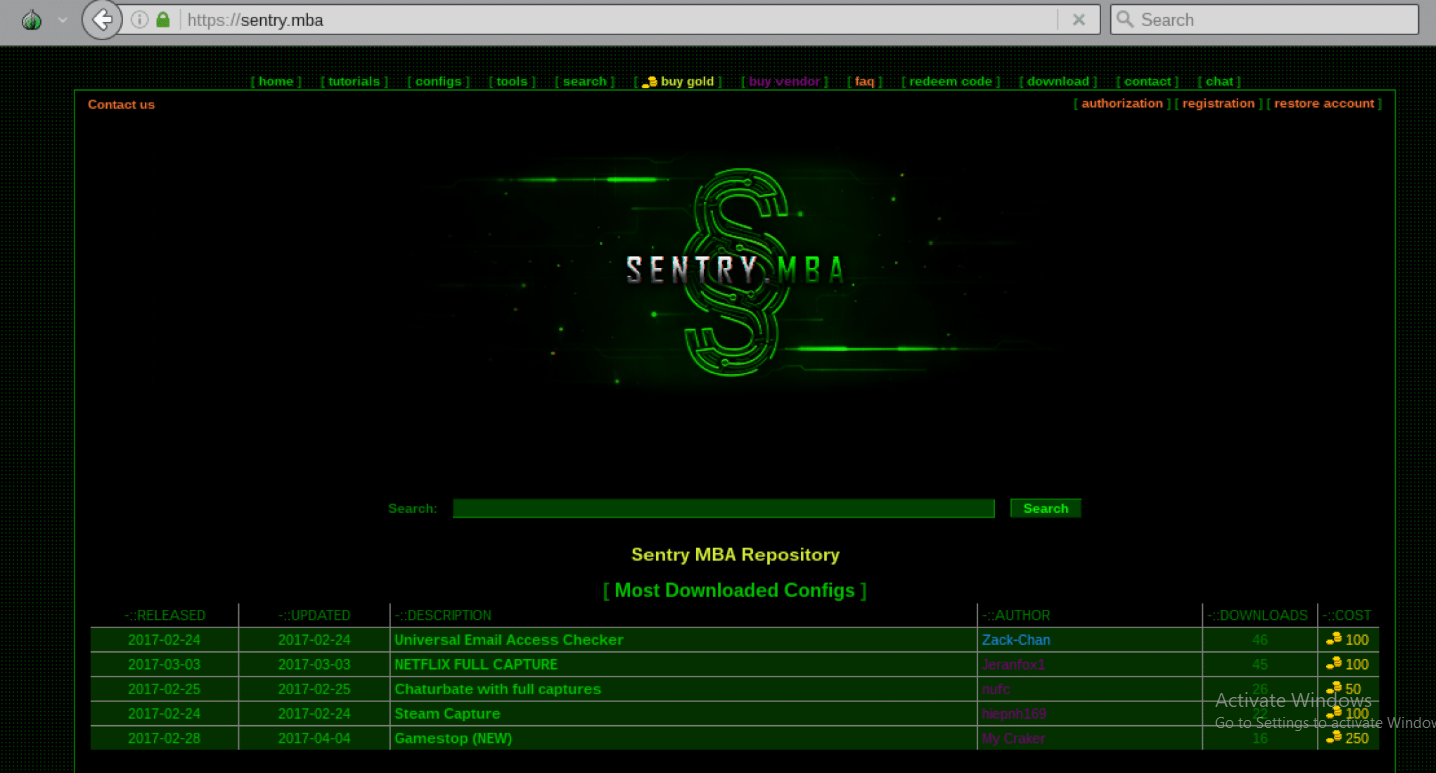
Sentry MBA 1.4.1 Cracked
Automated credential-testing tools have become a cornerstone of modern cyberattacks, enabling threat actors to breach online accounts at an unprecedented scale. Among these tools, modified versions of legitimate security testing software pose a particular threat when weaponized by malicious actors. These cracked or repurposed tools often incorporate enhanced evasion capabilities and underground exploit modules not […]
All Mail Brute 2025
Email account breaches remain one of the most damaging and prevalent threats in cybersecurity, serving as gateways to corporate espionage, financial fraud, and identity theft. Automated credential-cracking tools have become increasingly sophisticated, evolving to bypass modern security measures, such as multi-factor authentication (MFA) and account lockout policies. The 2025 generation of these attack platforms demonstrates […]
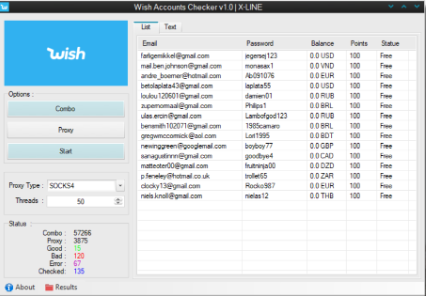
WISH ACCOUNT CHECKER 2025
The rise of e-commerce platforms has led to a corresponding surge in cybercriminal tools designed to exploit these digital marketplaces. Among these threats, automated WISH ACCOUNT CHECKER 2025 have become particularly prevalent in 2025, allowing attackers to systematically test stolen credentials against retail platforms. These tools serve as the first stage in sophisticated fraud chains, allowing […]
Smtp Checker 2025
Email remains one of the most critical communication channels for both individuals and organizations, making email infrastructure a prime target for cybercriminals. In 2025, specialized tools designed to test and exploit Smtp Checker 2025 (Simple Mail Transfer Protocol) servers have become increasingly sophisticated, playing a pivotal role in modern cyberattacks. These tools enable threat actors […]
Multi VPN Checker 2025
In 2025, multi-VPN checkers have become a double-edged sword in cybersecurity. While legitimate users rely on them to verify VPN functionality and privacy, threat actors increasingly exploit these tools to conduct sophisticated cyberattacks. By testing multiple VPN connections, attackers can identify weak points, evade geo-restrictions, and mask their malicious activities. Multi VPN Checker 2025 makes […]
Netflix Ultimate Cracking Pack 2025
In 2025, credential-cracking tools designed for streaming platforms have evolved into a significant cybersecurity threat. Netflix Ultimate Cracking Pack 2025 tools, often marketed as a means to bypass paid subscriptions, are increasingly weaponized for large-scale credential-stuffing attacks, identity theft, and financial fraud. By exploiting weak authentication mechanisms and leaked credential databases, attackers can hijack accounts, […]
XTOOL V3 CRACKED 22 IN 1 MULTI CHECKER
In the evolving landscape of cybercrime, multi-checker tools—particularly cracked versions—have become a favored asset for attackers looking to exploit stolen credentials, evade detection, and automate fraudulent activities. XTOOL V3 CRACKED 22 tools, often distributed through underground forums, enable cybercriminals to validate large batches of login credentials, payment cards, or compromised accounts across multiple platforms at […]
Smtp Checker 2024
In 2024, SMTP checkers have become a critical tool for cybercriminals engaged in email-based attacks, including phishing, spam campaigns, and credential brute-forcing. Smtp Checker 2024 tools allow attackers to verify the validity of email accounts by testing them against Simple Mail Transfer Protocol (SMTP) servers, ensuring that only active addresses are targeted in large-scale attacks. […]
BEST CRACKING PACK 2025
In 2025, comprehensive cracking toolkits have become a pervasive threat in the cybercriminal ecosystem, enabling attackers to automate credential theft, system breaches, and data exfiltration at scale. Best cracking pack 2025 all-in-one packages bundle multiple exploitation tools into a single interface, lowering the technical barrier for would-be attackers while increasing the efficiency of experienced hackers. […]