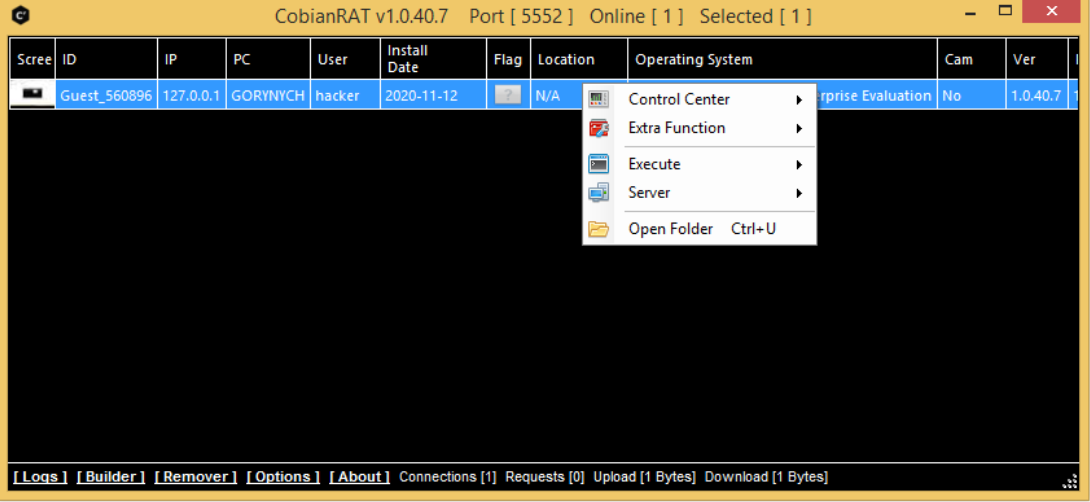
CobianRAT v1.0.40.7 with Tutorial
CobianRAT v1.0.40.7 is a powerful and versatile Remote Administration Tool (RAT) designed for remote system management, surveillance, and administrative tasks. It provides users with extensive control over a target machine, making it a popular choice among IT administrators, cybersecurity professionals, and ethical hackers. However, due to its capabilities, it can also be misused for malicious purposes, so ethical and legal considerations must be prioritized.
What is CobianRAT v1.0.40.7?
CobianRAT is a Windows-based remote administration tool that allows users to control a computer from a remote location. It operates as a client-server application, where the server (victim) runs silently in the background, while the client (attacker/administrator) sends commands and receives data. While it can be used for legitimate purposes like IT support and system monitoring, its misuse can lead to unauthorized access, making it a potential cybersecurity threat.
Feature | Description |
|---|---|
| Remote Desktop Control | View and control the victim’s desktop in real-time. |
| File Manager | Browse, upload, download, delete, and modify files on the infected system. |
| Keylogger | Records all keystrokes to capture sensitive data like passwords. |
| Process Manager | View running processes, terminate or start them remotely. |
| Webcam & Microphone Access | Activate the webcam and mic to monitor the victim’s environment. |
| Password Recovery | Extract saved passwords from web browsers and supported apps. |
| Persistent Connection | Maintains access even after system reboots. |
| Anti-Detection Techniques | Uses obfuscation and encryption to bypass antivirus software. |
| Remote Shell Access | Execute commands via a remote command-line interface. |
| Clipboard Monitoring | Monitors and logs copied content from the system clipboard. |
| Spread via USB | Propagates through USB or other removable drives automatically. |
Why Use CobianRAT v1.0.40.7?
While CobianRAT has legitimate uses in IT administration and cybersecurity testing, its misuse for illegal activities is a major concern. Ethical hackers and penetration testers may use it to assess system vulnerabilities, but unauthorized access is illegal and punishable by law. Always ensure proper authorization before deploying such tools.


