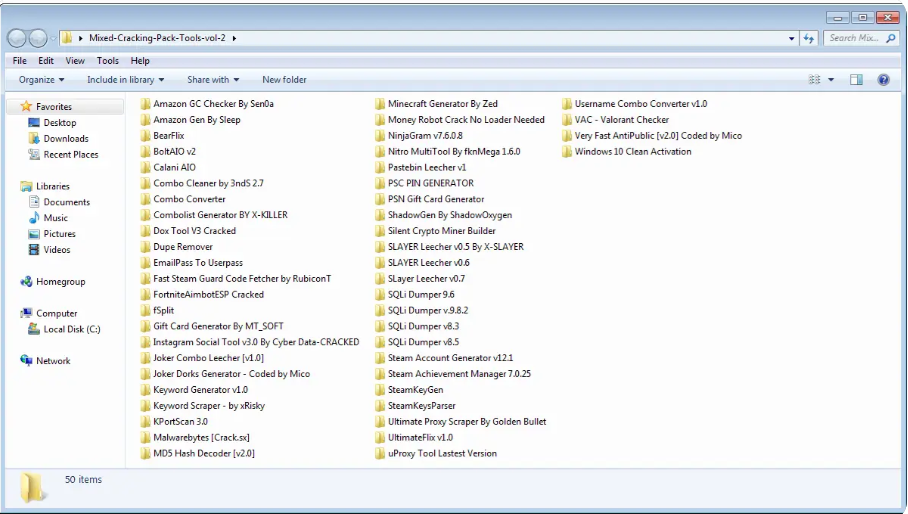
Cracking Tools Mega Pack 2025
The Cracking Tools Mega Pack 2025 is a comprehensive collection of advanced cybersecurity tools designed for penetration testers, ethical hackers, and security researchers. This all-in-one toolkit provides cutting-edge solutions for vulnerability assessment, password cracking, network analysis, and exploit development, making it an indispensable resource for cybersecurity professionals.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What Is Cracking Tools Mega Pack 2025?
The Cracking Tools Mega Pack compiles the latest and most powerful security tools for ethical hacking and penetration testing. It features software for brute-force attacks, decrypting hashes, sniffing networks, analyzing malware, and more. The developers regularly update the pack with new exploits and techniques to help users stay ahead of emerging cyber threats.
| Feature | Description |
|---|---|
| Password Cracking | Uses tools like Hashcat, John the Ripper, and Hydra for brute-force and dictionary attacks. |
| Network Penetration | Includes Wireshark, Nmap, Metasploit, and Aircrack-ng for scanning, sniffing, and exploiting networks. |
| Vulnerability Scanning | Integrates OpenVAS, Nessus, and Burp Suite for automated security assessments. |
| Exploit Development | Offers Immunity Debugger, Ghidra, and ROPgadget for reverse engineering and exploit creation. |
| Malware Analysis | Provides Cuckoo Sandbox, IDA Pro, and PEiD for analyzing and dissecting malware. |
| Wireless Hacking | Features Kismet and Fern Wi-Fi Cracker for auditing and exploiting wireless networks. |
| Forensic Tools | Includes Autopsy, Volatility, and FTK Imager for digital forensic investigations. |
| Custom Scripts & Payloads | Contains pre-built Python, PowerShell, and Bash scripts for automation and post-exploitation. |
Why Use Cracking Tools Mega Pack 2025?
This toolkit is essential for cybersecurity professionals who need to test system defences, identify vulnerabilities, and strengthen security measures. Whether you’re conducting a penetration test, performing red team exercises, or studying ethical hacking, this pack saves time by providing all necessary tools in one place. It is also invaluable for educational purposes, helping students and researchers understand real-world attack vectors and defence mechanisms.