Crypto Stealer 2025 Cracked
The cryptocurrency ecosystem faces growing threats from increasingly sophisticated malware, with Crypto Stealer 2025 Cracked emerging as one of the most dangerous tools for digital asset theft. This advanced malware variant demonstrates how cybercriminals are leveraging cracked versions of commercial stealers to create powerful, low-cost attack tools. Crypto Stealer 2025 Cracked has been actively used in campaigns targeting both individual investors and cryptocurrency businesses, showcasing how specialized malware can bypass security measures to directly steal digital currencies. Its ability to manipulate transactions and exfiltrate wallet data while evading detection makes it a significant concern in today’s cryptocurrency landscape.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What is the Crypto Stealer
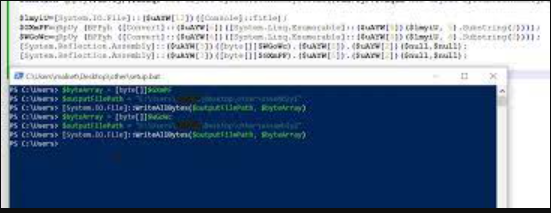
This software is a specialized cryptocurrency stealer designed to target wallet applications, browser extensions, and transaction processes. Unlike generic information stealers, it incorporates blockchain-specific features to identify and hijack cryptocurrency-related data. Typically distributed through fake crypto trading tools, malicious wallet apps, or phishing sites, it focuses on extracting private keys, seed phrases, and clipboard contents. Cybercriminals primarily use it to redirect transactions and steal funds directly from victims’ wallets, often resulting in irreversible financial losses due to the nature of blockchain transactions.
Key Features
| Feature | Description |
| Wallet File Detection | Scans for and steals cryptocurrency wallet.dat files |
| Browser Extension Theft | Targets MetaMask, Trust Wallet, and other browser-based wallets |
| Clipboard Hijacking | Monitors and replaces cryptocurrency addresses during copy-paste operations |
| Transaction Interception | Alters pending transactions before blockchain confirmation |
| Private Key Extraction | Recovers keys from installed wallet applications |
| Multi-Currency Support | Works with Bitcoin, Ethereum, and 50+ other cryptocurrencies |
| Process Injection | Executes malicious code within legitimate crypto apps |
| Anti-Analysis | Detects and evades sandbox environments and security tools |
| Encrypted C2 | Uses secure communication channels with command servers |
How the Crypto Stealer Works
The malware follows a targeted approach designed specifically for cryptocurrency theft:
1. Delivery & Infection
- Spreads via fake cryptocurrency apps on third-party stores.
- Bundled with cracked trading software on torrent sites.
- Delivered through phishing emails pretending to be from exchanges.
2. Initial Execution
- Performs environment checks for virtual machines.
- Verifies that cryptocurrency-related software is installed.
- Drops payload in system temp folders with random names.
3. Data Collection
Wallet Targeting:
- Scans for wallet files in common storage locations.
- Extracts private keys and seed phrases.
- Targets browser extension wallets through cookie theft.
Transaction Monitoring:
- Hooks into clipboard operations to replace addresses.
- Intercepts API calls to cryptocurrency exchanges.
- Alters transaction confirmation dialogs.
4. Fund Exfiltration
- Immediately transfers stolen funds to:
- Mixer services for obfuscation.
- Intermediate wallets before consolidation.
- Exchange accounts under attacker control.
5. Persistence & Evasion
- Creates scheduled tasks for regular execution.
- Uses process hollowing to hide in legitimate apps.
- Implements gas fee manipulation to prioritize malicious transfers.
- Self-destructs after completing theft.


