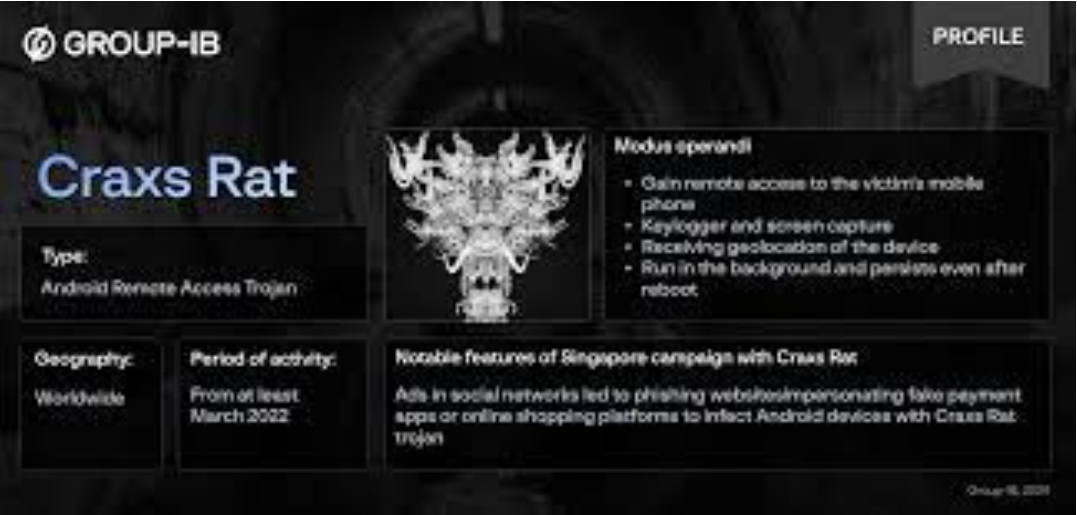
Cypher Rat 2025 cracked
In recent years, cybercriminals have increasingly relied on sophisticated information-stealing malware to compromise sensitive data. One such tool, often referred to as “X-FILES STEALER 2025,” has gained notoriety for its ability to evade detection while exfiltrating credentials, financial data, and other valuable information. These stealers are frequently distributed through phishing campaigns, malicious downloads, or exploit kits, making them a persistent threat to individuals and organizations alike. Once deployed, they can harvest data from browsers, cryptocurrency wallets, and even installed applications, feeding stolen information back to attackers for further exploitation.
Download Link 1
Download Link 2
Download Link 3
This type of malware is designed to collect and exfiltrate sensitive data from infected systems silently. It typically operates as a standalone executable or an injected module within legitimate processes to avoid detection. Every day, use cases include credential theft, financial fraud, and corporate espionage. Attackers often deploy it in targeted attacks or sell it on underground forums, where less technically skilled criminals can leverage its capabilities.
Key Features of Cypher Rat 2025
| Feature | Description |
| Browser Data Theft | Extracts saved passwords, cookies, and autofill data from major browsers. |
| Cryptocurrency Theft | Scans for and steals wallet files and private keys from crypto applications. |
| System Information | Collects hardware details, OS version, and installed software. |
| Keylogging | Logs keystrokes to capture credentials and other typed information. |
| Anti-Detection | Uses process injection and obfuscation to evade antivirus software. |
| Exfiltration | Sends stolen data to a C2 (Command and Control) server via encrypted channels. |
How Cypher Rat 2025 Works
Infection and Execution
The malware typically infiltrates a system through social engineering tactics, such as disguised email attachments or fake software cracks. Once executed, it may employ persistence mechanisms, such as registry modifications or scheduled tasks, to ensure it survives reboots. To avoid detection, it often injects its payload into legitimate processes (e.g., explorer.exe or svchost.exe) using techniques such as process hollowing or DLL Injection.
Data Collection Techniques of Cypher Rat 2025
The stealer scans the system for specific files and directories associated with browsers (Chrome, Firefox, Edge), cryptocurrency wallets (Electrum, Exodus), and messaging apps (Telegram, Discord). It extracts:
- Browser Data: Decrypts and retrieves stored passwords, cookies, and credit card details using SQLite queries or dedicated decryption modules.
- File Grabbing: Targets documents (PDFs, Word files) and wallet.dat files based on predefined paths.
- Keylogging: Captures keystrokes in real-time to obtain additional credentials.
Exfiltration and C2 Communication
Stolen data is usually compressed, encrypted, and transmitted to a remote C2 server via HTTPS or FTP to avoid network-level detection. Some variants utilize domain generation algorithms (DGAs) to dynamically switch C2 servers, making takedowns challenging.
Evasion Tactics
To hinder analysis, the malware may:
- Check for Sandboxes/VMs: Terminates execution if it detects virtualized environments.
- Use Packers/Obfuscation: Encrypts its code to bypass static analysis.
- Disable Security Tools: Kills processes related to antivirus or monitoring software.


