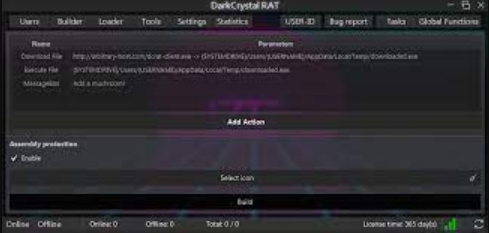
DCRat v1.0.7 Auto Build
The cybersecurity threat landscape continues to evolve with increasingly accessible malware tools, and DcRat v1.0.7 Auto Build has emerged as a particularly concerning example of democratized cyberattack capabilities. This automated remote access tool demonstrates how cybercriminals are lowering the technical barriers to sophisticated attacks through user-friendly malware builders. DcRat v1.0.7 Auto Build has been widely distributed in underground forums, enabling even novice attackers to conduct surveillance operations and system compromises. Its automated build system and extensive feature set have made it popular among cybercriminals for credential theft, financial fraud, and unauthorized system access, posing significant challenges for traditional security defenses.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is the DcRat v1.0.7 Auto Build
This software is an automated remote access trojan (RAT) builder that allows attackers to create customized malware payloads with minimal technical knowledge. The tool generates executable files that provide complete control over infected systems, including file management, screen capture, and keylogging capabilities. Typically distributed through underground hacking communities, the builder creates payloads that are often delivered via phishing emails, malicious downloads, or fake software updates. Cybercriminals primarily use it for stealing sensitive information, conducting surveillance, and maintaining persistent access to compromised systems. The auto-build functionality enables rapid generation of unique malware variants, making signature-based detection particularly challenging.
Key Features
| Feature | Description |
| Automated Payload Generation | Creates unique malware executables with one-click building |
| Remote Desktop Control | Provides real-time access to victim systems |
| Keylogging | Captures all keyboard inputs to steal credentials |
| File Management | Enables uploading, downloading, and deleting files |
| Screen Capture | Takes screenshots of victim’s activities |
| Process Manipulation | Allows killing or spawning system processes |
| Persistence | Maintains access through registry modifications and startup entries |
| Encrypted C2 | Uses secure communication channels with command servers |
How the DcRat v1.0.7 Auto Build Works
The malware operates through a streamlined infection and control process:
1. Payload Creation
Attackers use the builder to:
- Configure C2 server connections.
- Select desired features (keylogging, screen capture, etc.).
- Set persistence mechanisms.
- Generate unique payload executables.
2. Delivery & Infection
The generated payload spreads through:
- Phishing emails with malicious attachments.
- Compromised websites with drive-by downloads.
- Trojanized software is distributed on file-sharing platforms.
The infection process:
- Drops components in %Temp% or system directories.
- Modifies registry keys for persistence.
- Injects into legitimate processes.
3. Core Functionality
Once executed, the malware:
Establishes connection to C2 server.
Implements selected features:
- Logs keystrokes and screenshots.
- Provides remote shell access.
- Monitors system activities.
Maintains heartbeat with C2 infrastructure.
4. Data Exfiltration
Stolen information is transmitted via:
- Encrypted HTTP/HTTPS channels.
- Compressed and encoded data packets.
- Multiple fallback C2 servers.
5. Evasion Techniques
The malware employs:
- Code obfuscation to hinder analysis.
- Process hollowing to hide malicious activity.
- Legitimate-looking network traffic.
- Sandbox detection to delay malicious activity.


