Diabolic Traffic Bot Full Edition v8.0 Activated
Automated tools that manipulate web traffic pose a growing challenge for cybersecurity professionals. Among these, traffic generation bots are particularly concerning. Diabolic traffic bot simulate human-like interactions to overwhelm websites, distort analytics, or commit fraud. Often, attackers use them in distributed denial-of-service (DDoS) attacks, ad fraud, or competitive sabotage. Because they mimic legitimate users at scale, they usually evade basic detection. As a result, organizations must adopt advanced mitigation strategies to address these challenges.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
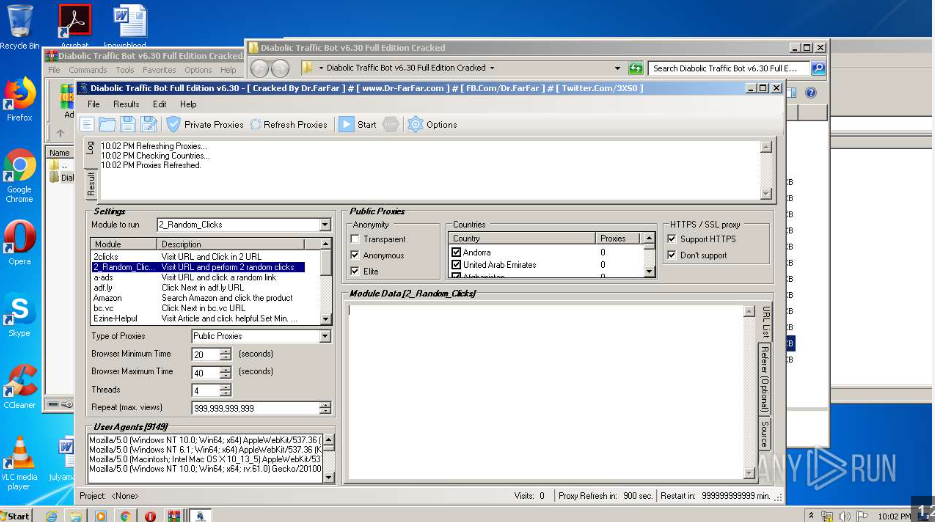
This software is a sophisticated tool for generating traffic. It simulates high volumes of web requests from multiple sources, including proxies and virtual users. While designed for stress testing, malicious actors exploit it to disrupt services, inflate ad revenue, or skew marketing data. Additionally, it supports customizable request patterns, IP rotation, and browser emulation to appear legitimate. Some organizations use similar tools ethically for load testing. However, unauthorized deployments often violate the terms of service and can result in legal consequences.
Key Features of Diabolic Traffic Bot
| Feature | Description |
|---|---|
| Proxy Support | Route traffic through multiple IPs to avoid detection. |
| User-Agent Spoofing | Mimics various browsers and devices to blend in with organic traffic. |
| Request Customization | Allows fine-tuned control over HTTP headers, cookies, and request rates. |
| Session Persistence | Maintains fake user sessions to appear more authentic. |
| DDoS Capabilities | Overwhelms targets with high request volumes, resulting in degraded performance. |
| Analytics Manipulation | Injects false data into tracking systems to distort metrics. |
How Diabolic Traffic Bot Works
The software deploys virtual users, often distributed across proxy servers or botnets, to generate traffic toward a target. To evade detection, it uses advanced techniques:
IP Rotation. It cycles through multiple proxy servers or VPNs, masking its origin and making IP-based blocking difficult.
Browser Emulation. Each virtual user mimics a real browser with randomized user-agent strings, screen resolutions, and JavaScript execution, bypassing basic bot filters.
Request Throttling:. Traffic is sent at controlled intervals to avoid sudden spikes that trigger rate-limiting defenses.
Session Simulation: The bot maintains cookies and follows navigation paths (e.g., clicking links or submitting forms) to imitate real user behavior.
By employing these methods, the tool effectively blends in with legitimate traffic, making detection and mitigation more challenging.