DORK PREMIUM PACK 2024
Cybercriminals are increasingly leveraging automated tools to identify and exploit vulnerable web assets at scale. These DORK PREMIUM PACK 2024 search systems enable attackers to efficiently discover sensitive data, unprotected systems, and exploitable web applications across the internet. By automating the process of finding security gaps, these tools dramatically reduce the time between reconnaissance and exploitation, making them particularly dangerous in the hands of both skilled hackers and less-technical threat actors. Their ability to continuously scan for newly exposed vulnerabilities makes them a persistent threat to organizations of all sizes, contributing to data breaches, website defacements, and unauthorized access incidents.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
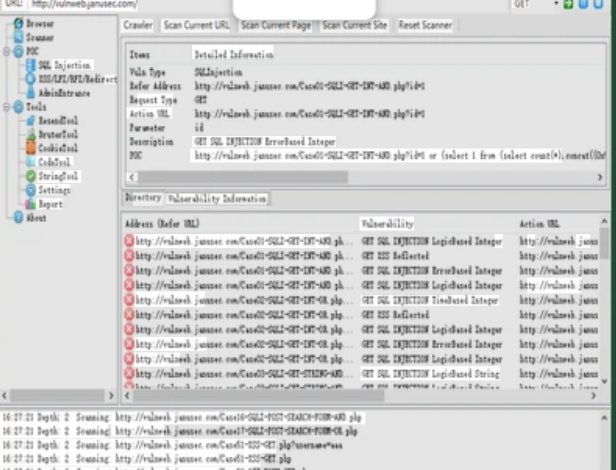
This software is an advanced web vulnerability discovery system that automates the process of finding exploitable targets through specialized search techniques. It combines sophisticated query generation with results filtering to identify websites with specific security weaknesses or exposed sensitive information. Typically used by penetration testers, security researchers, and unfortunately cybercriminals, the tool helps uncover vulnerable web applications, open directories, exposed databases, and improperly secured administrative interfaces. The software’s effectiveness lies in its ability to parse through massive amounts of web data while minimizing false positives, making it a powerful tool for both defensive and offensive security purposes.
Key Features of DORK PREMIUM PACK 2024
| Feature | Description |
| Smart Query Generator | Creates targeted search strings for specific vulnerabilities |
| Result Validator | Automatically verifies found vulnerabilities |
| Proxy Integration | Supports rotating proxy servers for anonymous scanning |
| API Scraper | Identifies exposed API endpoints and documentation |
| CMS Detector | Recognizes specific content management system versions |
| Data Pattern Matching | Finds exposed credentials, config files, and sensitive documents |
| Export Formats | Generates reports in multiple formats for further analysis |
How DORK PREMIUM PACK 2024 Works
The system operates through a multi-stage process to identify and validate potential targets:
- Target Identification Phase
- Generates specialized search queries combining:
- Known vulnerability indicators
- Common misconfiguration patterns
- Platform-specific file structures
- Submits queries through multiple search engines
- Parses results while avoiding detection mechanisms
- Preliminary Filtering
- Applies regex patterns to filter irrelevant results
- Checks for basic accessibility (HTTP status codes)
- Identifies potentially interesting file types:
- Configuration files (.env, config.php)
- Backup files (.bak, .zip)
- Database dumps (.sql)
- Log files (.log)
- Vulnerability Verification
- Performs non-intrusive checks to confirm findings:
- Directory listing verification
- Default credential testing
- Unauthenticated access attempts
- Version disclosure analysis
- Rates discovered vulnerabilities by potential impact
- Result Organization
- Categorizes findings by vulnerability type
- Groups related assets by domain/IP
- Prioritizes based on exploitability
- Generates actionable reports