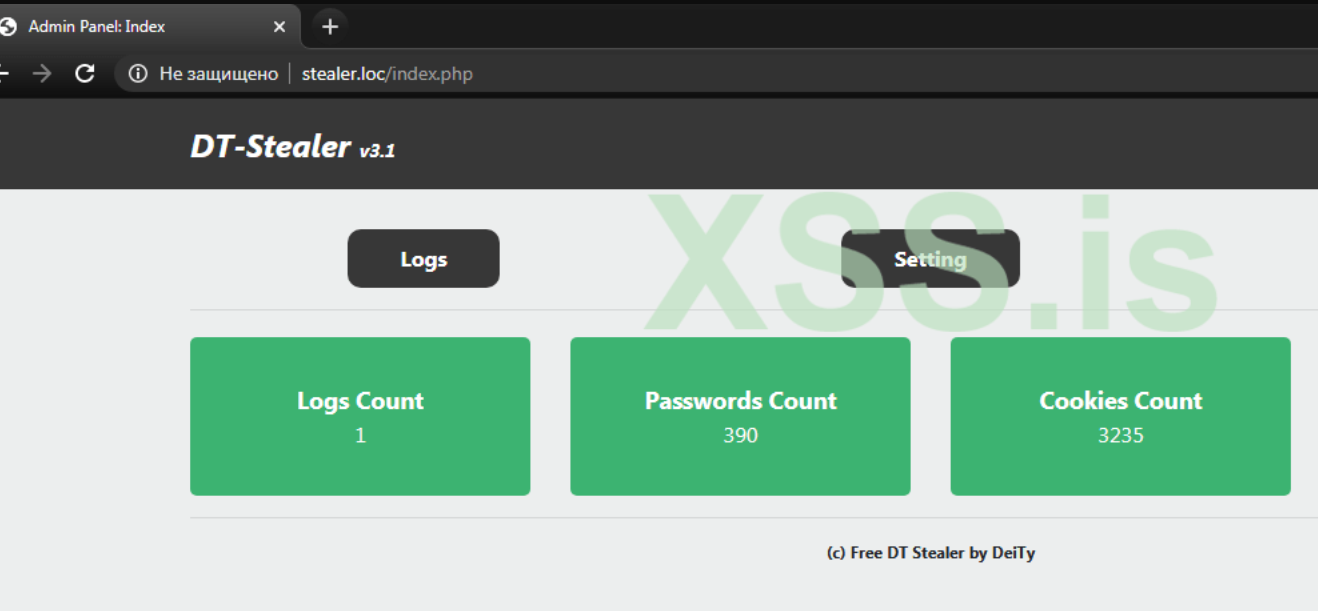
DT Stealer V1.3 with Source
DT Stealer V1.3 is a powerful information-stealing malware designed to extract sensitive data from compromised systems. With its open-source availability, it has gained attention among cybersecurity researchers and threat actors alike. This article delves into its functionality, features, and the risks it poses.
Download Link 1
Download Link 2
Download Link 3
What is DT Stealer V1.3?
DT Stealer V1.3 is a malicious software tool developed to harvest credentials, cookies, browser history, cryptocurrency wallets, and other critical data from infected machines. The malware operates stealthily, evading detection while exfiltrating stolen information to a remote server controlled by the attacker. Its open-source nature allows for customization, making it a versatile tool for cybercriminals.
| Feature | Description |
|---|---|
| Credential Theft | Extracts saved passwords from web browsers such as Chrome, Firefox, Edge, and Opera. |
| Cookie Hijacking | Steals session cookies to bypass authentication and gain unauthorized account access. |
| Cryptocurrency Wallet Grabber | Target wallet files like Exodus and Electrum, including private keys for crypto theft. |
| System Information Logger | Collects system data such as OS version, hardware specifications, and installed software. |
| Keylogging Capability | Logs user keystrokes to capture sensitive information such as passwords and messages. |
| Discord Token Stealer | Extracts Discord authentication tokens to enable full account takeover. |
| Anti-Debugging & VM Detection | Detects and avoids sandbox or virtual machine environments used for malware analysis. |
| File Grabber | Searches for and uploads specific file types such as documents, images, and databases. |
| Persistent Installation | Installs itself to survive reboots and maintain long-term access to the system. |
| Custom C2 Support | Enables attacker-defined command & control server configurations for data exfiltration. |
Why Use DT Stealer V1.3?
While primarily used for malicious purposes, DT Stealer V1.3 is also studied by cybersecurity professionals to understand its attack vectors and improve defensive measures. However, its misuse can lead to severe financial and data breaches. Awareness of its capabilities helps organizations strengthen their security posture against such threats.


