Ez Dork Gen DELUXE Edition 2025
Ez Dork Gen DELUXE also known as Google hacking, is a widely used technique for uncovering hidden vulnerabilities, exposed databases, and misconfigured web applications. Advanced threat generation tools streamline this process by automating the creation of targeted search queries, allowing both attackers and security professionals to identify exploitable targets quickly. While ethical hackers utilize these tools for vulnerability assessments, cybercriminals exploit them to identify weaknesses, such as SQL injection vulnerabilities, exposed admin panels, and sensitive data leaks. As cyber defences improve, so do these tools, incorporating AI-driven query optimization and evasion techniques to bypass search engine restrictions.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
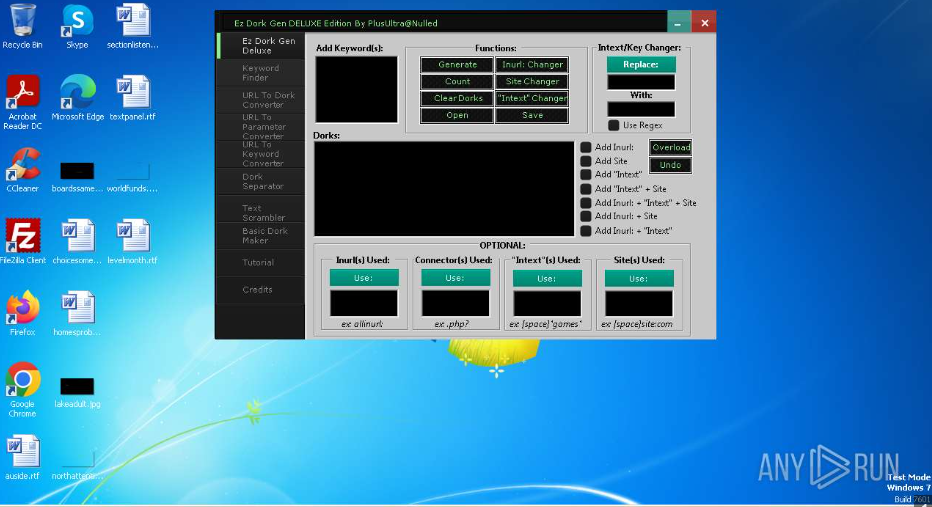
This tool is designed to automate and enhance the process of crafting specialized search queries (dorks) that locate vulnerable websites, open directories, or exposed sensitive files. It helps penetration testers efficiently discover security flaws, but in the hands of malicious actors, it can accelerate reconnaissance for attacks such as data breaches, credential harvesting, and website defacement. The software often includes prebuilt dark web libraries, customizable filters, and integration with other scanning tools to maximize effectiveness.

Key Features of Ez Dork Gen DELUXE
| Feature | Description |
| AI-Optimizeds Dork Generation | Uses machine learning to refine search queries for better results. |
| Preloaded Dork Libraries | Includes categorized dorks (e.g., SQLi, XSS, login pages, exposed cameras). |
| Custom Query Building | Allows manual input and combination of operators. |
| Search Engine Integration | Works with Google, Bing, and other search engines while avoiding CAPTCHAS and blocks. |
| Proxy & TOR Support | Enables anonymous searching to prevent IP-based restrictions. |
| Export & Reporting | Saves results in formats like CSV/TXT for further analysis. |
| API & Tool Integration | Can feed results into vulnerability scanners or SQLi exploitation tools. |
How the Ez Dork Gen DELUXE Works: Techniques & Functionality
Query Generation & Optimization
The process begins with a built-in database of known effective dorks. From there, users can customize their search queries using Boolean logic (AND, OR) and advanced operators to fine-tune results. In some cases, AI components may analyze recent attack patterns or target profiles to suggest high-yield targets, increasing the chances of uncovering vulnerable systems.
Search Engine Interaction
Once the queries are ready, the software sends them to search engines while applying rate-limiting techniques to avoid triggering security filters. As results come in, the tool parses them efficiently, filtering out irrelevant links and instead prioritizing those that match the user’s selected parameters.
Target Validation & Refinement
After filtering, detected URLs are validated for potential signs of vulnerabilities—such as exposed error messages or default login pages. To reduce noise, the software cross-references these results with a list of known secure sites, helping minimize false positives and focus on true threats.
Payload Delivery (Optional Integration)
If integrated with an exploitation module, the software can move beyond scanning and begin testing for vulnerabilities directly:
It may test for SQL injection (SQLi) by appending malicious payloads to input fields.
It can check for cross-site scripting (XSS) vulnerabilities by injecting simple scripts.
Additionally, it identifies exposed directories and misconfigured server paths.
Reporting & Actionable Output
Finally, all findings are compiled into a structured report. The report includes risk ratings, organized results, and categorization of issues based on severity. Notably, high-value or easily exploitable targets may be flagged for immediate follow-up, allowing operators to act quickly and strategically.
![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)