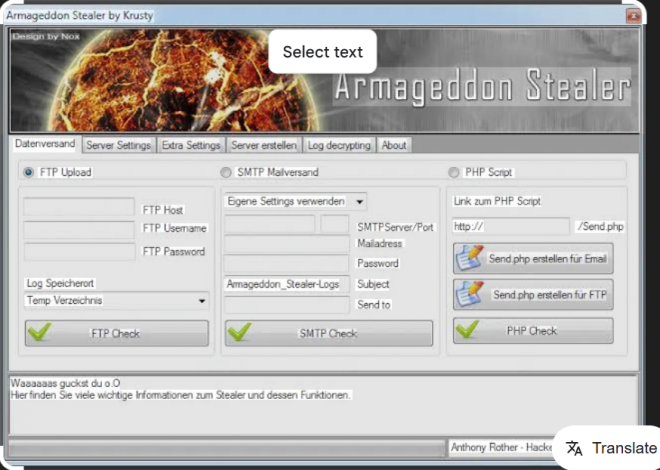
Eziriz Net Reactor 5.9.2.0
Eziriz Net Reactor is a powerful obfuscation and protection tool designed to secure .NET applications from reverse engineering and unauthorized modifications. While it serves as a valuable resource for developers, its robust capabilities have also made it a favored choice among threat actors aiming to conceal malicious code, evade detection, and deploy payloads in cyberattacks. In fact, security researchers have observed its use in various campaigns, where it helps malware bypass both static and dynamic analysis by employing advanced obfuscation techniques. Typically, its scan range includes .NET assemblies, allowing it to modify and protect executable files, which significantly complicates analysis for defenders.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
On the surface, this software is primarily marketed as a legitimate solution for developers seeking to protect their intellectual property by preventing decompilation and tampering. To achieve this, it transforms .NET binaries into heavily obfuscated versions that are extremely difficult to analyze. For example, common legitimate applications include safeguarding proprietary business software, licensing systems, and sensitive algorithms. However, malicious actors exploit these same features to hide malware—such as stealers, ransomware, and remote access trojans (RATs)—within seemingly harmless .NET applications. As a result, distinguishing between legitimate and malicious use of Net Reactor remains a significant challenge for cybersecurity professionals.
Key Features
| Feature | Description |
| Code Obfuscation | Renames symbols, encrypts strings, and alters control flow to hinder analysis. |
| Anti-Debugging | Detects and disrupts debugging attempts to prevent dynamic analysis. |
| Anti-Tampering | Checks for modifications to the protected binary and triggers failsafes. |
| Virtualization | Converts .NET methods into virtualized instructions to obscure logic. |
| Packing & Compression | Reduces file size and further obscures the original code structure. |
| Watermarking | Embeds identifiers to track unauthorized distribution. |
How Eziriz Net Reactor Works
The software operates by taking a net executable as input and applying multiple layers of obfuscation to hinder analysis and detection. Below is a breakdown of its key techniques and functionality:
Code Transformation
- Renaming: Classes, methods, and variables are given meaningless names to disrupt readability.
- Control Flow Obfuscation: Logical structures (e.g., loops, conditionals) are rewritten into convoluted patterns, making static analysis difficult.
- String Encryption: Sensitive strings (e.g., URLs, commands) are encrypted and only decrypted at runtime.
Anti-Analysis Measures
- Debugger Detection: The software checks for attached debuggers and may terminate or alter execution if one is detected.
- Sandbox Evasion: It may probe system environments (e.g., checking for virtualized or analysis tools) before executing payloads.
Payload Delivery
- Staged Execution: Malicious payloads are often split into multiple layers, with each stage decrypting and loading the next only when specific conditions are met.
- Dynamic Loading: Some variants fetch additional payloads from remote servers at runtime, reducing the malware’s footprint in initial scans.
Persistence Mechanisms
- If used maliciously, the obfuscated binary may employ techniques like registry modifications or scheduled tasks to maintain persistence on infected systems.