Falcon Keylogger 2025 Cracked
The threat landscape continues to evolve with increasingly sophisticated surveillance tools, and Falcon Keylogger 2025 Cracked has emerged as one of the most dangerous information-stealing malware variants in modern cyberattacks. This advanced keylogging software demonstrates how cybercriminals are leveraging cracked commercial spyware to conduct large-scale credential theft campaigns. Falcon Keylogger 2025 Cracked has been actively used in attacks targeting businesses, government agencies, and individual users, showcasing its ability to bypass security measures while harvesting sensitive input data. Its enhanced stealth capabilities and comprehensive logging features make it particularly effective for capturing login credentials, financial information, and private communications without detection.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is the Falcon Keylogger
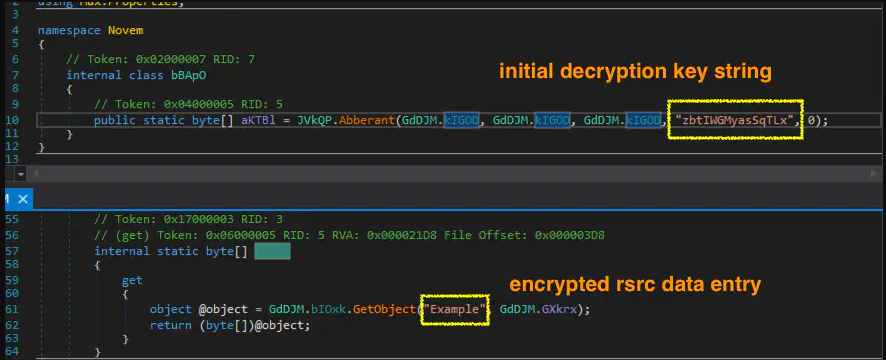
This software is a sophisticated keylogger designed to covertly record and exfiltrate keystrokes, screenshots, and clipboard activity from infected systems. Unlike basic keyloggers, it incorporates advanced evasion techniques to avoid detection by security software while maintaining persistent access. Typically distributed through phishing emails, malicious downloads, or trojanized software installers, the malware targets Windows systems and actively monitors user input across applications, browsers, and login portals. Cybercriminals primarily use it for credential harvesting, financial fraud, and corporate espionage, with stolen data often sold on underground markets or used for further attacks.
Key Features
| Feature | Description |
| Keystroke Logging | Records all keyboard inputs, including passwords and messages |
| Screen Capture | Takes periodic screenshots of active applications |
| Clipboard Monitoring | Captures copied text, including cryptocurrency addresses |
| Process Injection | Runs within legitimate processes to evade detection |
| Data Exfiltration | Sends stolen information to remote servers via encrypted channels |
| Persistence | Maintains access through registry modifications or task scheduling |
| Anti-Analysis | Detects and exits virtualized or monitored environments |
How the Falcon Keylogger Works
The malware employs a multi-stage approach to ensure stealth and effectiveness:
1. Delivery & Infection
- Spreads via malicious email attachments (e.g., DOC, PDF, or EXE files).
- Bundled with pirated software on torrent sites or crack forums.
- Distributed through fake update prompts on compromised websites.
2. Installation & Persistence
- Drops payload in temporary system folders with randomized names.
- Creates registry autorun entries for persistence.
- Injects into trusted processes (e.g., explorer.exe).
- Implements watchdog processes to ensure continuous operation
3. Data Collection
Keystroke Logging:
- Captures inputs across all applications, including browsers and email clients..
- Records timestamps and application context for each entry.
Screen Capture:
- Takes screenshots during login sessions or specific activities.
- Compresses images to reduce file size.
Clipboard Monitoring:
- Logs copied text, particularly targeting cryptocurrency addresses.
4. Data Exfiltration
- Compresses and encrypts logs before transmission
- Uses multiple exfiltration methods:
- Encrypted HTTPS to C2 servers.
- Cloud storage sync (e.g., Google Drive, Dropbox).
- Email or Telegram bots for immediate access.
5. Evasion Techniques
- Code obfuscation to avoid signature detection.
- Legitimate process mimicry (e.g., disguising as a system utility).
- Low CPU usage to prevent performance alerts.
- Sandbox detection to delay malicious activity.


