Gaudox Botnet v1.1.0.1
Gaudox Botnet v1.1.0.1 is a sophisticated modular botnet framework designed for large-scale cyber operations, including DDoS attacks, credential harvesting, and cryptocurrency mining. This updated version introduces enhanced encryption, improved command-and-control (C2) resilience, and plugin-based functionality, allowing hackers to deploy customized attack modules on infected machines. Its multi-platform compatibility (Windows, Linux) and stealthy propagation make it a significant threat to both individual users and enterprise networks.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What is Gaudox Botnet v1.1.0.1?
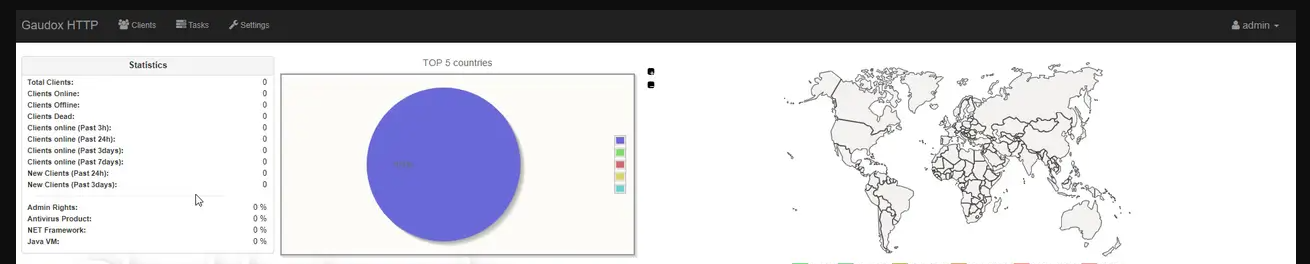
Gaudox Botnet v1.1.0.1 is a malware-as-a-service (MaaS) toolkit sold in underground forums, enabling hackers to build and manage a decentralized botnet. Unlike traditional botnets, Gaudox uses peer-to-peer (P2P) communication for C2 resilience, making takedowns difficult. The botnet supports on-demand plugin loading, meaning new attack capabilities (e.g., ransomware, spyware) can be deployed without reinstalling the core malware.
Detailed Features of Gaudox Botnet v1.1.0.1
| Feature Category | Technical Specifications |
|---|---|
| Botnet Architecture | Hybrid P2P + centralized C2 for redundancy |
| Infection Vectors | Exploits (RDP, EternalBlue), phishing, drive-by downloads |
| Attack Modules | Plugins for DDoS, cryptomining, ransomware, data theft |
| DDoS Capabilities | UDP/TCP/HTTP floods (up to 1.5 Tbps with sufficient bots) |
| Credential Harvesting | Steals browser passwords, FTP logins, and SSH keys |
| Persistence | Rootkit installation, hidden cron jobs (Linux), registry hooks (Windows) |
| Evasion Techniques | Code obfuscation, VM/sandbox detection, TLS-encrypted C2 traffic |
| Self-Propagation | Scans for vulnerable devices on local networks |
| Update Mechanism | Silent background updates for new attack modules |
| Geofencing | Avoids infecting systems in specific countries (configurable) |
Why Do Hackers Use Gaudox Botnet v1.1.0.1?
- High Profit Potential – Monetization via DDoS-for-hire, crypto mining, or stolen data sales.
- Resilient Infrastructure – P2P architecture prevents single-point takedowns.
- Flexible Attack Options – Plugins allow quick adaptation to new threats.
- Low Resource Usage – Operates silently to avoid detection.
- Easy Management – Web-based admin panel for botnet control.


