GhostDZ RAT v1.1D
The GhostDZ RAT v1.1D has emerged as a significant threat in modern cyberattacks, particularly due to its stealthy infiltration capabilities and persistence mechanisms. Often deployed in targeted attacks, this malware enables threat actors to gain long-term access to compromised systems, exfiltrate sensitive data, and execute malicious commands remotely. Its ability to evade detection while maintaining a low profile makes it a favored tool among cybercriminals and espionage groups. As defenses improve, GhostDZ continues to evolve, incorporating new evasion techniques and modular functionalities to stay ahead of security measures.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

Overview of the GhostDZ RAT v1.1D
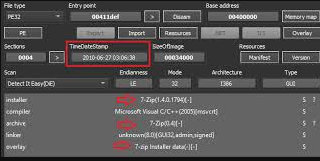
GhostDZ is a sophisticated Remote Access Trojan (RAT) designed to provide attackers with full control over infected systems. Typically distributed through phishing campaigns, malicious attachments, or drive-by downloads, it operates covertly to avoid raising suspicion. Once installed, it enables functionalities such as keylogging, screen capturing, file theft, and remote command execution. Its modular design allows attackers to customize its features based on their objectives, making it adaptable for espionage, financial theft, or further network infiltration.
Key Features
| Feature | Description |
| Remote Control | Allows attackers to execute commands and control the infected system in real time. |
| Keylogging | Logs keystrokes to capture passwords, messages, and other sensitive input. |
| Screen Capture | Takes screenshots to monitor user activity and gather visual data. |
| File Exfiltration | Steals and uploads files from the infected system to a remote server. |
| Persistence | Maintains long-term access via registry modifications, scheduled tasks, or service installations. |
| Process Injection | Hides malicious activity by running code within legitimate processes. |
| Encrypted C2 Communication | Uses secure channels (HTTPS, DNS tunneling) to communicate with attacker-controlled servers. |
| Anti-Analysis | Detects sandbox environments and debugging tools to avoid detection. |
How the GhostDZ RAT v1.1D Works
The malware follows a multi-stage infection process to ensure stealth and persistence while avoiding detection by security software.
Infection & Initial Execution
- Phishing Emails.
- Fake Software Installers.
- Exploit Kits.
Once executed, the malware may
- Decrypt & Deploy.
- Escalate Privileges.
- Disable Security Tools.
Persistence & Evasion
- Registry Modifications.
- Scheduled Tasks.
- Process Hollowing.
Command & Control (C2) Communication
- HTTPS Traffic.
- DNS Tunneling.
- Dynamic IP Rotation.
Payload Execution & Data Theft
- Credential Harvesting.
- File Theft.
- Remote Shell Access.


