HACK PACK Crypters, Binders, Keyloggers
In the evolving landscape of cyber threats, attackers frequently employ tools such as crypters, binders, and keyloggers to facilitate malicious activities. These components often come bundled in “HACK PACK Crypters,” providing cybercriminals with the ability to obfuscate malware, combine malicious payloads with legitimate files, and stealthily capture sensitive user data. Threat actors leverage such tools in targeted attacks, credential theft, and ransomware campaigns, posing a persistent challenge to cybersecurity defenses. The ability of crypters to evade detection and deliver payloads undetected underscores the need to understand their mechanics to develop effective countermeasures.
Download Link 1
Download Link 2
Download Link 3
Key Features of Hack Pack Crypters
| Feature | Description |
|---|---|
| Encryption | Obfuscates malware code to evade signature-based detection. |
| Payload Binding | Combines malicious payloads with benign files to bypass user suspicion. |
| Keylogging | Captures keystrokes to steal credentials, messages, and other sensitive data. |
| Persistence | Ensures malware remains active after system reboots. |
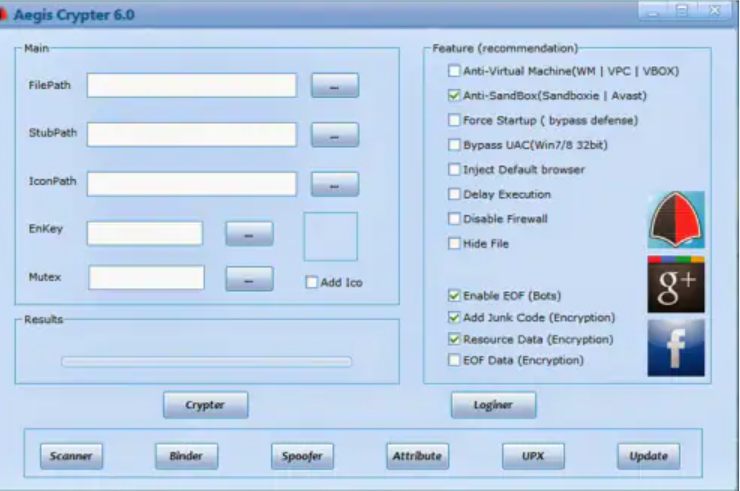
| Anti-Debugging | Detects and avoids analysis in sandboxed or debugged environments. |
| Rootkit Capabilities | Hides processes, files, and registry entries to maintain stealth. |
How Hack Pack Crypters Work
Obfuscation (Crypting)
The crypter uses encryption algorithms (e.g., AES, XOR) to scramble the malware’s code, altering its signature and evading antivirus detection. Some variants apply polymorphic techniques, dynamically changing the code structure with each execution.
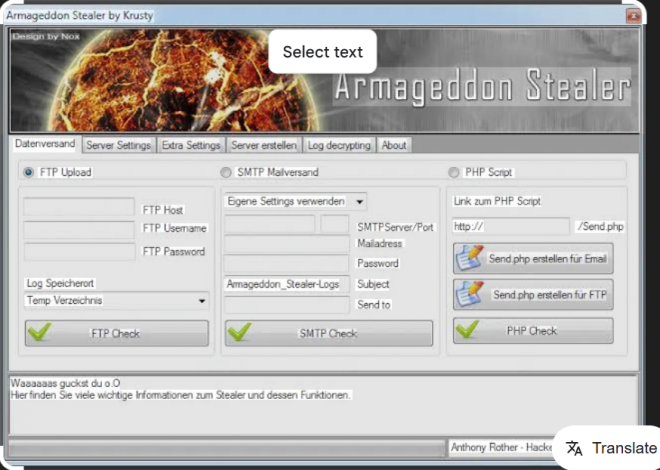
Payload Delivery (Binding)
The binder embeds the malicious payload within a legitimate file, such as an installer or document. When the user opens the file, the binder extracts and executes the payload—either in memory or on disk—often using techniques like DLL injection or process hollowing to blend into trusted processes.
Keylogging
The keylogger hooks into system APIs to monitor keyboard inputs. It logs data to a file or transmits it to a command-and-control (C2) server via HTTP, FTP, or encrypted channels. Some variants also capture screenshots or clipboard data.
Persistence Mechanisms
To maintain long-term access, the malware may:
Modify registry keys,
Create scheduled tasks, or
Install itself as a service.
These techniques ensure execution persists after system reboots.
Evasion Tactics
Anti-sandboxing checks detect virtualized environments.
Anti-debugging tricks (e.g., timing delays) hinder analysis.
Rootkit functionalities hide files, processes, and network connections from security tools.