HACK PACK Crypters, Binders, Keyloggers and more
Modern cybercriminals increasingly rely on all-in-one attack toolkits that bundle multiple malicious capabilities into single, easy-to-use platforms. These Swiss Army knife-style packages have become particularly dangerous as they democratize advanced attack techniques, enabling even low-skilled threat actors to launch sophisticated campaigns. By combining HACK PACK crypter, binder, and keylogger functionalities with automated deployment mechanisms, these toolkits significantly lower the barrier to entry for cybercrime while simultaneously increasing the effectiveness of attacks. Their modular nature allows for customization to specific targets, making them popular choices for everything from credential theft to ransomware deployment across both enterprise and consumer targets.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
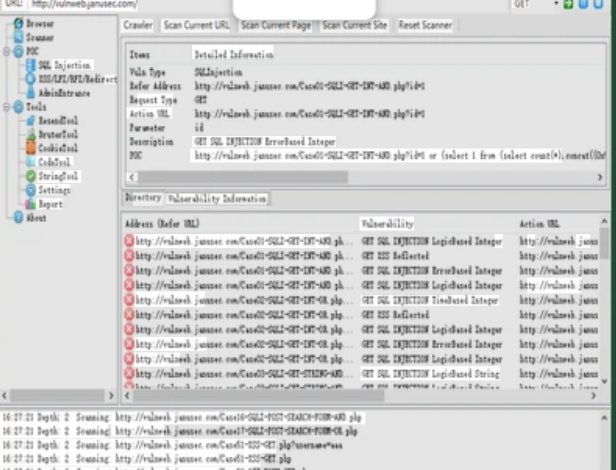
This software represents a comprehensive malicious toolkit designed to provide end-to-end attack capabilities in a single package. It combines multiple offensive security tools with an intuitive interface that guides users through each stage of an attack chain. Cybercriminals typically use it to create undetectable malware variants, bundle malicious payloads with legitimate files, and monitor victim activity through various surveillance methods. The toolkit’s popularity stems from its ability to bypass modern security controls while requiring minimal technical expertise from operators, making it particularly prevalent in credential harvesting campaigns, financial fraud operations, and targeted espionage activities.

Key Features
| Feature | Description |
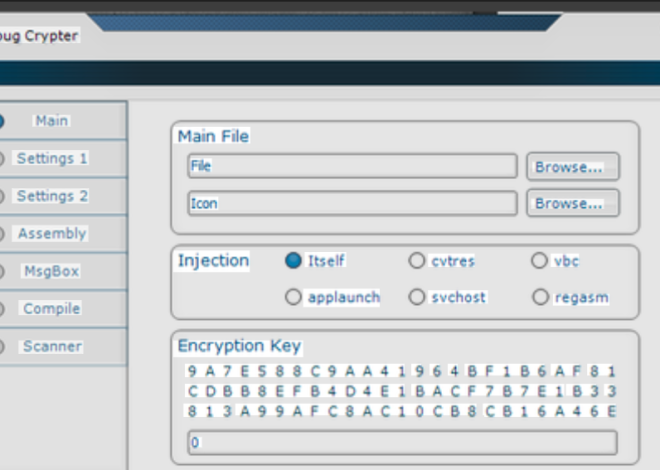
| Advanced Crypter | Polymorphic encryption with FUD (Fully Undetectable) capabilities |
| Smart Binder | Seamless integration of payloads with legitimate executables |
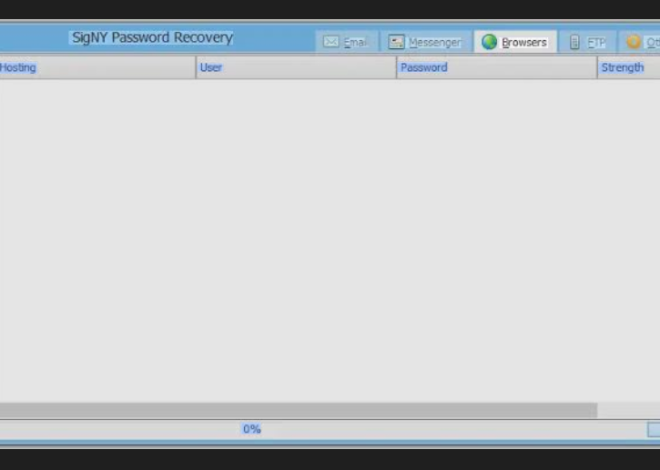
| Keylogger | Stealthy input capture with form-grabbing functionality |
| Anti-Analysis | Built-in sandbox and virtual machine detection |
| Payload Factory | Generates multiple malware types from single interface |
| Traffic Masking | Encrypted C2 communications mimicking cloud services |
| Self-Destruct | Automatic artifact removal after execution |
How HACK PACK Works
The toolkit operates through an integrated workflow that automates complex attack processes:
- Payload Preparation Phase
- Users select from various malware templates (RATs, infostealers, ransomware)
- The crypter module applies multiple transformation layers:
- AES-256 encryption for core payload protection
- Runtime unpacking stub with polymorphic code
- PE header manipulation to evade static analysis
- The binder merges the payload with legitimate host files:
- Preserves original file functionality
- Implements thread hijacking for stealth execution
- Uses checksum maintenance to appear authentic
- Delivery & Execution Phase
- Generates customized delivery mechanisms:
- Weaponized documents with macro triggers
- Fake software installers
- Compromised system utilities
- Implements advanced execution techniques:
- Process hollowing (replacing legitimate process memory)
- DLL sideloading (abusing trusted application dependencies)
- COM hijacking (manipulating Windows component objects)
- Post-Infection Operations
- The keylogger module activates with multiple capture methods:
- Keyboard hooking for traditional logging
- Form grabbing for web credential theft
- Screen capture for visual monitoring
- Establishes persistence through:
- Scheduled tasks masquerading as system updates
- Registry modifications in obscure locations
- Service installation with deceptive names
- Data Exfiltration Phase
- Uses multiple redundant communication channels:
- HTTPS tunnels disguised as browser traffic
- DNS tunneling for restricted environments
- Cloud storage APIs for blending with legitimate traffic
- Implements data compression and encryption before transmission
- Self-destructs temporary components post-exfiltration