Hap Crypter Cracked 2024
Hap Crypter is a well-known software crypter designed to obfuscate malicious executables, making them undetectable by antivirus programs. The “cracked” 2024 version refers to an illicitly modified release, often distributed in underground forums. While it has legitimate uses in penetration testing, its misuse poses significant cybersecurity threats. This article explores its functionality, risks, and defensive measures.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What is Hap Crypter Cracked 2024?
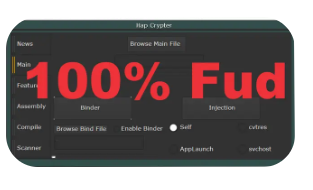
Hap Crypter is a crypting tool used to encrypt, bind, and modify executable (EXE) files to evade detection. The 2024 cracked version implies an unauthorized, freely distributed copy, often bundled with hidden payloads. Ethical hackers may study it for malware analysis, but its primary misuse involves bypassing security software to deliver malware.
Detailed Features of Hap Crypter Cracked 2024
| Feature Category | Description |
|---|---|
| File Obfuscation | Encrypts EXE files using AES, RC4, or custom algorithms. |
| Compresses payloads to reduce file size and avoid heuristic detection. | |
| AV & Sandbox Evasion | Bypasses signature-based detection in antivirus programs. |
| Detects and exits in virtual machines (VMs) and sandboxes. | |
| Payload Binding | Merges multiple executables into a single file (e.g., malware + legit app). |
| Persistence Mechanisms | Can enable auto-start registry entries for long-term access. |
| Customizable Options | Allows icon, version info, and manifest spoofing for social engineering. |
| Stub Generation | Creates a custom decryption stub to unpack malware at runtime. |
| C2 Communication | Some variants include hidden C2 callbacks for remote control. |
Why Use Hap Crypter Cracked 2024? (For Research & Defense)
While misused by hackers, security professionals study Hap Crypter to:
- Understand evasion techniques used in modern malware.
- Improve antivirus detection by analyzing crypting methods.
- Train in ethical hacking by reverse engineering such tools in controlled environments.
Download Link 1
Download Link 2
Download Link 3
Download Link 4