Hellfire Yahoo Checker 2025
In 2025, credential-stuffing and account-checking tools remain a major threat to online security, particularly targeting legacy email platforms like Yahoo. Hellfire Yahoo Checker 2025 allows attackers to verify large volumes of stolen credentials, enabling unauthorized access to accounts for identity theft, financial fraud, or further exploitation. As older email services often lack modern security measures like mandatory multi-factor authentication (MFA), automated checkers pose a significant risk, making them a common tool in the arsenal of cybercriminals.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
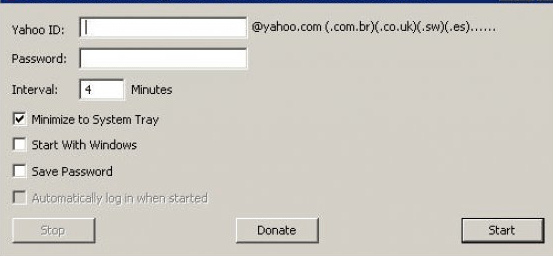
This software is designed to automate the process of testing Yahoo email account credentials for validity. It checks whether a given username and password combination is active by attempting to log in to Yahoo’s authentication system. While legitimate security researchers may use such tools to identify compromised accounts, attackers typically leverage them to validate stolen credentials before selling them or using them in further attacks. The software often includes features like proxy support, request throttling, and bulk list processing to maximize efficiency while avoiding detection.
Key Features
| Feature | Description |
| Bulk Credential Checking | Tests thousands of username-password pairs in rapid succession. |
| Proxy & VPN Integration | Rotates IP addresses to bypass rate limits and avoid blacklisting. |
| Request Throttling | Adjusts request speed to mimic human behavior and evade detection. |
| Multi-threaded Processing | Speeds up validation by running multiple login attempts simultaneously. |
| Custom User-Agent Spoofing | Masquerades as legitimate browsers to avoid security filters. |
| Results Filtering | Exports only valid credentials, discarding failed attempts for efficiency. |
How Hellfire Yahoo Checker 2025 Works
The software operates by systematically testing Yahoo account credentials through automated login attempts. Below is a detailed breakdown of its functionality:
- Input & Preparation
The attacker loads a list of email and password combinations (often obtained from data breaches). The software may format and clean the list to remove duplicates or malformed entries. - Connection & Authentication
The tool sends login requests to Yahoo’s authentication servers, mimicking a legitimate browser session. It typically uses HTTPS to avoid network-level detection. - Response Analysis
The software analyzes Yahoo’s response to determine whether the credentials are valid:- Successful Login: The account is marked as active and logged for further use.
- Failed Attempt: The credentials are discarded or flagged for retesting.
- Rate-Limited or Blocked: The tool may switch proxies or pause before retrying.
- Evasion Techniques
To avoid triggering Yahoo’s security systems, the software may:- Rotate through proxy servers to distribute requests.
- Randomize delays between login attempts.
- Spoof user-agent strings to appear as different devices.
- Payload & Post-Exploitation
Once valid credentials are identified, attackers may:- Harvest sensitive data (emails, contacts, recovery info).
- Use the account for phishing or spam campaigns.
- Sell verified credentials on dark web marketplaces.


