Hooker Keylogger 2024
Hooker Keylogger 2024 is a robust and discreet surveillance software designed to monitor and record keystrokes, user activities, and system interactions. Due to its versatility, it is used for both legitimate and illicit purposes, making it a controversial yet effective tool in digital monitoring.

What Is Hooker Keylogger?
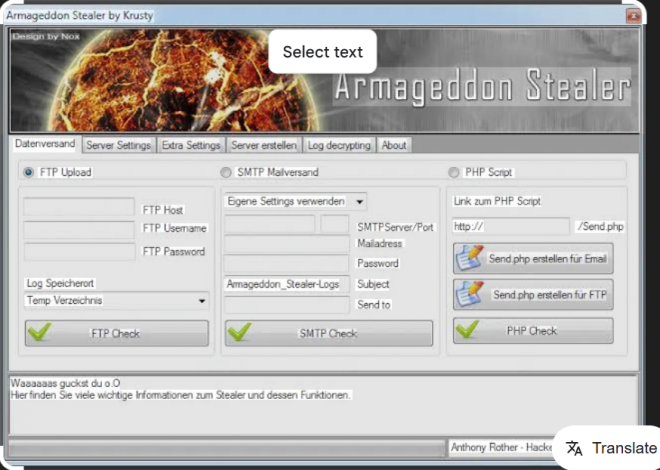
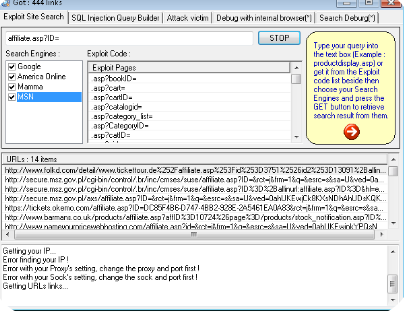
Hooker Keylogger is an advanced keylogging program that runs silently in the background, capturing every keystroke on the targeted device. Beyond keystroke recording, it captures screenshots, clipboard data, browsing history, and credentials entered into applications. Its stealth capabilities help it evade detection by most antivirus solutions, making it a popular choice for covert monitoring.
Key Features of Hooker Keylogger 2024
| Feature | Description |
|---|---|
| Keystroke Logging | Records all typed inputs, including passwords, chats, emails, and search queries. |
| Screen Capture | Takes periodic or triggered screenshots to visually track user activities. |
| Clipboard Monitoring | Captures any text copied to the clipboard for detailed monitoring. |
| Application Tracking | Logs which applications are in use and their active duration. |
| Remote Data Delivery | Sends logged data securely to a predefined email or FTP server for remote access. |
| Stealth Mode | Runs invisibly, hidden from task managers and antivirus programs. |
| Encrypted Logs | Stores all collected data in encrypted files to prevent unauthorized access. |
| Custom Triggers | Activates logging based on specific keywords, applications, or user-defined conditions. |
| Cross-Platform Compatibility | Supports Windows, macOS, and select Linux distributions for versatile deployment. |
| User Session Recording | Tracks user login/logout times and active session durations for comprehensive monitoring. |
Why Use Hooker Keylogger 2024?
This software can be used for various legitimate purposes such as parental control, employee monitoring, and cybersecurity research. However, it also carries a risk of misuse for malicious activities including identity theft and corporate espionage. Ethical deployment requires explicit authorization, as unauthorized use may result in legal penalties.