Hooker Keylogger 2024
In an era where digital security and surveillance are paramount, Hooker Keylogger 2024 emerges as a powerful tool designed for discreet monitoring. Whether for parental control, employee oversight, or personal security, this advanced keylogger offers unmatched stealth and functionality.
What Is Hooker Keylogger 2024?
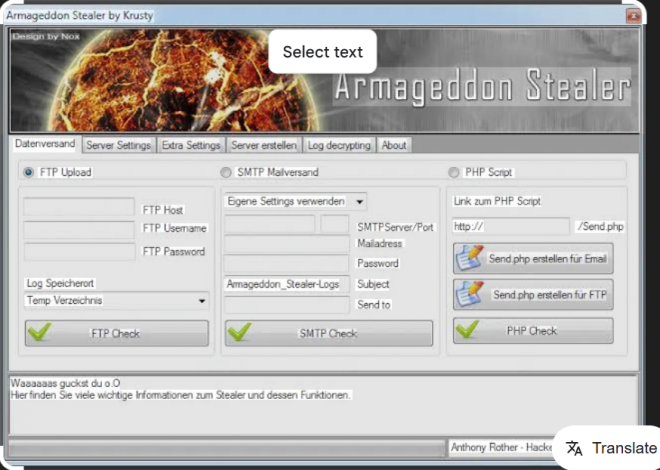
Hooker Keylogger is a cutting-edge surveillance software that records keystrokes, captures screenshots, and monitors user activity on a target device. It operates invisibly in the background, making it undetectable to the user. This tool is widely used for legitimate purposes, such as ensuring cybersecurity, tracking employee productivity, or supervising children’s online activities.
Detailed Features
| Feature | Description |
|---|---|
| Keystroke Logging | Records every keystroke typed, including passwords, messages, and search queries. |
| Stealth Mode | Runs invisibly without appearing in the task manager or system tray. |
| Screenshot Capture | Takes periodic screenshots to provide visual context of user activity. |
| Remote Monitoring | Sends logs to a secure email or FTP server for remote access. |
| Clipboard Monitoring | Tracks copied text, including sensitive data like credit card numbers. |
| Application Tracking | Logs opened applications and websites visited, including incognito mode. |
| File and Document Tracking | Monitors file access, downloads, and modifications. |
| Time-Stamped Logs | Organizes recorded data with accurate timestamps. |
| Password Protection | Restricts access to the keylogger’s control panel with a password. |
| Compatibility | Compatible with Windows 10/11 and supports multiple languages. |
Why Use Hooker Keylogger 2024?
Hooker Keylogger 2024 is ideal for parents who want to protect their children from online threats, employers monitoring work efficiency, or individuals securing their devices against unauthorized access. Its advanced features ensure comprehensive tracking while maintaining complete secrecy. However, ethical and legal considerations must be observed—always use such tools responsibly and with consent where required.