ICG Auto Exploiter BoT 2025
In the evolving landscape of cybersecurity threats, automated exploitation tools have become a significant concern for defenders. Among these, the ICG Auto Exploiter BoT represents a sophisticated example of modern malware designed to identify and exploit vulnerabilities with minimal human intervention. Such tools are frequently employed in large-scale cyberattacks, enabling threat actors to compromise systems, deploy payloads, and establish persistence rapidly. Their automation capabilities make them particularly dangerous, as they can scan and exploit targets at scale, often before patches or mitigations are applied.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
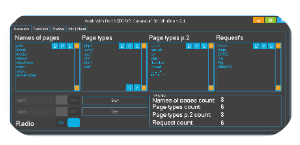
This software is a modular, automated exploitation framework designed to streamline the process of identifying and exploiting vulnerabilities in target systems. Typically used by malicious actors, it combines reconnaissance, vulnerability scanning, and payload delivery into a single workflow. Its primary uses include gaining unauthorized access, deploying ransomware, stealing sensitive data, or integrating compromised systems into botnets. The tool is often distributed through phishing campaigns, malicious downloads, or compromised websites, and it operates with a focus on evasion and persistence.
Key Features of ICG Auto Exploiter BoT
| Feature | Description |
| Automated Scanning | Scans networks and systems for known vulnerabilities. |
| Exploit Database Integration | Leverages a built-in database of exploits for rapid attack execution. |
| Payload Customization | Allows attackers to tailor payloads (e.g., ransomware, spyware) for delivery. |
| Anti-Detection Mechanisms | Uses obfuscation, encryption, and sandbox evasion to avoid detection. |
| Botnet Integration | Can link compromised systems to a command-and-control (C2) server. |
| Persistence Modules | Ensures continued access via registry edits, scheduled tasks, or rootkits. |
How the ICG Auto Exploiter BoT Works
1. Reconnaissance and Scanning
The tool initiates reconnaissance on the target network or system. It employs techniques such as port scanning, service fingerprinting, and vulnerability probing to identify potential entry points. For example, it might scan for open Remote Desktop Protocol (RDP) ports or outdated web applications with known exploits.
2. Exploit Selection and Execution
Once a vulnerability is detected, the software references its integrated exploit database to select the appropriate attack method. It then automates the exploitation process, injecting malicious code or commands to compromise the target. Standard techniques include buffer overflow attacks, SQL injection, or leveraging unpatched software flaws.
3. Payload Delivery and Execution
After exploitation, the tool delivers a payload tailored to the attacker’s objectives. This could be a remote-access trojan (RAT), ransomware, or a data exfiltration script. Payloads are often delivered via encrypted channels to evade detection, and they may be staged to avoid triggering security alerts.
4. Persistence and Lateral Movement
To maintain access, the software deploys persistence mechanisms such as registry modifications, hidden scheduled tasks, or backdoor installations. If the target is part of a more extensive network, the tool may attempt lateral movement by exploiting additional systems using harvested credentials or network-based attacks.
5. Command and Control (C2) Communication
Compromised systems typically establish a connection to a Command and Control (C2) server, allowing the attacker to issue commands, update payloads, or exfiltrate data. Communication is often disguised as legitimate traffic (e.g., HTTPS) to bypass network monitoring.
By automating each stage of the attack chain, this software significantly reduces the time and expertise required to execute successful breaches, making it a potent tool in the hands of cybercriminals. Defending against such threats requires proactive patch management, network segmentation, and robust endpoint detection systems.
![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)