Kronus RAT 2024
Kronus RAT (Remote Access Trojan) is a powerful surveillance and remote-control tool that emerged in 2024. While marketed as a legitimate remote administration tool, it is often exploited by hackers for unauthorized access, data theft, and system manipulation. Its advanced evasion techniques and modular design make it a significant threat in cybersecurity.

What is Kronus RAT?
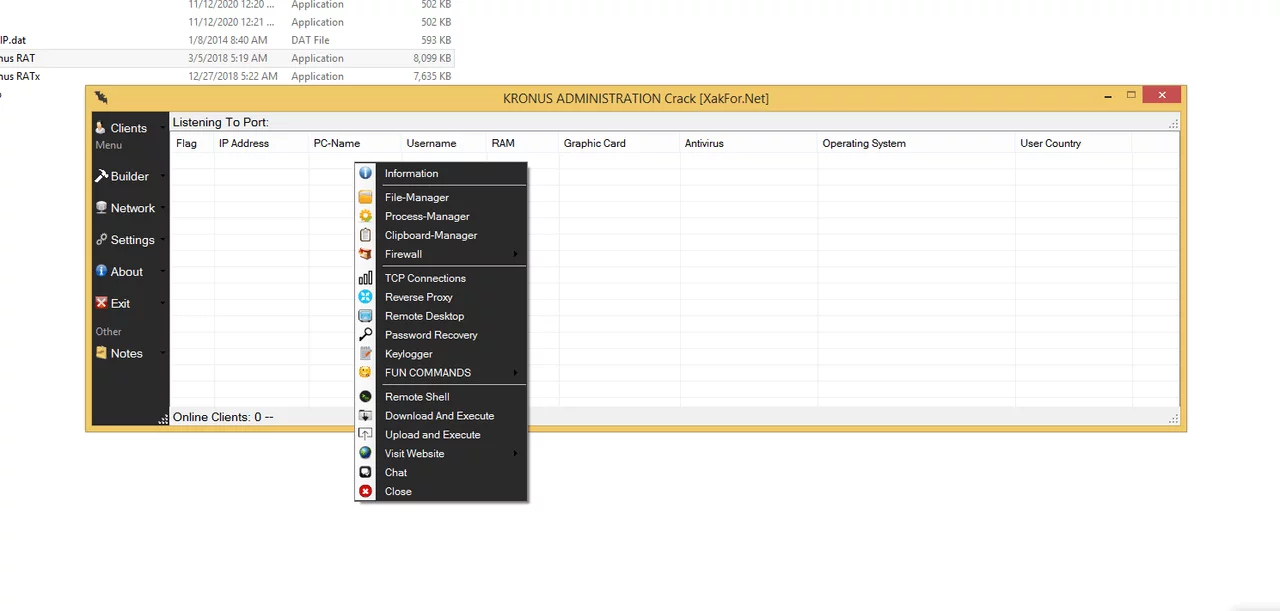
Kronus RAT is a Windows-based malware that allows attackers to remotely control infected systems. It operates stealthily, bypassing security measures to execute commands, steal sensitive data, and maintain persistence. Unlike traditional RATs, Kronus 2024 includes enhanced encryption, anti-detection mechanisms, and plugin support, making it harder to detect and remove.
Detailed Features of Kronus RAT 2024
The table below outlines its key functionalities:
| Feature Category | Description |
| Remote Control | Full desktop control, keyboard/mouse input, process management. |
| Data Theft | Extracts passwords, cookies, credit card info, and files from victim’s PC. |
| Persistence | Auto-starts with Windows via registry manipulation or task scheduling. |
| Evasion Techniques | Code obfuscation, VM/sandbox detection, and anti-debugging. |
| Network Propagation | Spreads via phishing emails, infected USB drives, or network vulnerabilities. |
| Plugin System | Supports add-ons like cryptocurrency miners, ransomware, or keyloggers. |
| Encrypted C2 | Command-and-control (C2) communications use AES-256 encryption. |
| Screen Capture | Records screen activity and takes screenshots without user knowledge. |
| Microphone/Webcam | Activates recording devices for spying. |
| File Manager | Uploads, downloads, or deletes files on the victim’s system. |
Why Do Hackers Use Kronus RAT?
- Stealth & Persistence: Operates undetected for long-term access.
- Multi-Functionality: Combines spying, data theft, and system control.
- Customizable: Plugins allow tailored attacks (e.g., ransomware deployment).
- Profit-Driven: Stolen data is sold on dark web markets.
- Low Detection Rates: Bypasses antivirus and endpoint protection.
Additional Risks & Protective Measures
- Victims can suffer financial loss, identity theft, and privacy breaches.
- Mitigation: Use updated antivirus, network monitoring, and avoid suspicious downloads.
- Education: Awareness of phishing tactics and secure browsing is critical.


