KYMS RAT v2.8 Cracked
KYMS RAT v2.8 Cracked is a modified remote administration tool that has become a subject of interest in cybersecurity research circles. While legitimate RATs serve valid purposes in IT administration, this cracked version is frequently analyzed by security professionals to understand modern attack methodologies. This examination focuses strictly on defensive cybersecurity applications, including threat analysis, detection methodology development, and ethical hacking education.

What is KYMS RAT v2.8 ?
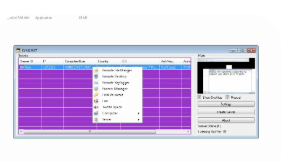
KYMS RAT is a sophisticated Windows-based Remote Access Trojan that provides extensive control over compromised systems. The cracked version removes licensing restrictions, making it valuable for authorized security research in:
- Malware behavioral analysis
- Attack vector identification
- Defensive countermeasure development
- Digital forensics training
Detailed Feature Analysis
| Feature Category | Technical Specifications |
|---|---|
| Remote Control | Full desktop view and control with mouse/keyboard input. |
| Surveillance | Webcam/microphone activation, screen recording. |
| Data Exfiltration | File transfer (upload/download), clipboard monitoring. |
| System Manipulation | Process termination, registry editing, service modification. |
| Persistence | Installation via registry keys, scheduled tasks, startup folders. |
| Security Evasion | Code obfuscation, anti-VM techniques, process hollowing. |
| Information Gathering | Keylogging, password extraction from browsers/mail clients. |
| Network Capabilities | Port forwarding, proxy support, encrypted C2 channels. |
| Customization | Configurable build options, plugin support. |
| Management | Multiple victim management through centralized panel. |
Why Do Hacker Use KYMS RAT v2.8 Cracked?
Defensive Cybersecurity
- Develop detection signatures for EDR solutions.
- Create behavioral analysis rules for SIEM systems.
Incident Response
- Train in forensic artifact identification.
- Practice malware eradication techniques.
Red Teaming
- Understand advanced persistence methods.
- Simulate real-world attack scenarios.
Academic Research
- Support malware reverse engineering courses.
- Contribute to threat intelligence databases.
Security Tool Development
- Improve anti-malware solutions.
- Enhance network monitoring capabilities.


