Laravel SMTP Checker 2025
As web applications increasingly rely on email functionality for user authentication, notifications, and communication, specialized tools have emerged to exploit vulnerabilities in these systems. The 2025 iteration of SMTP validation tools targeting Laravel-based applications represents a significant evolution in automated attack capabilities. These tools specifically exploit the email handling features of Laravel applications to verify valid email addresses, test SMTP configurations, and identify vulnerable systems. Their role in modern cyberattacks has expanded beyond simple credential stuffing to include sophisticated reconnaissance for targeted phishing campaigns, account takeover attempts, and as a gateway for more complex web application attacks. The growing popularity of Laravel SMTP Checker 2025 as a PHP framework has made applications built with it particularly attractive targets for these specialized exploitation tools.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
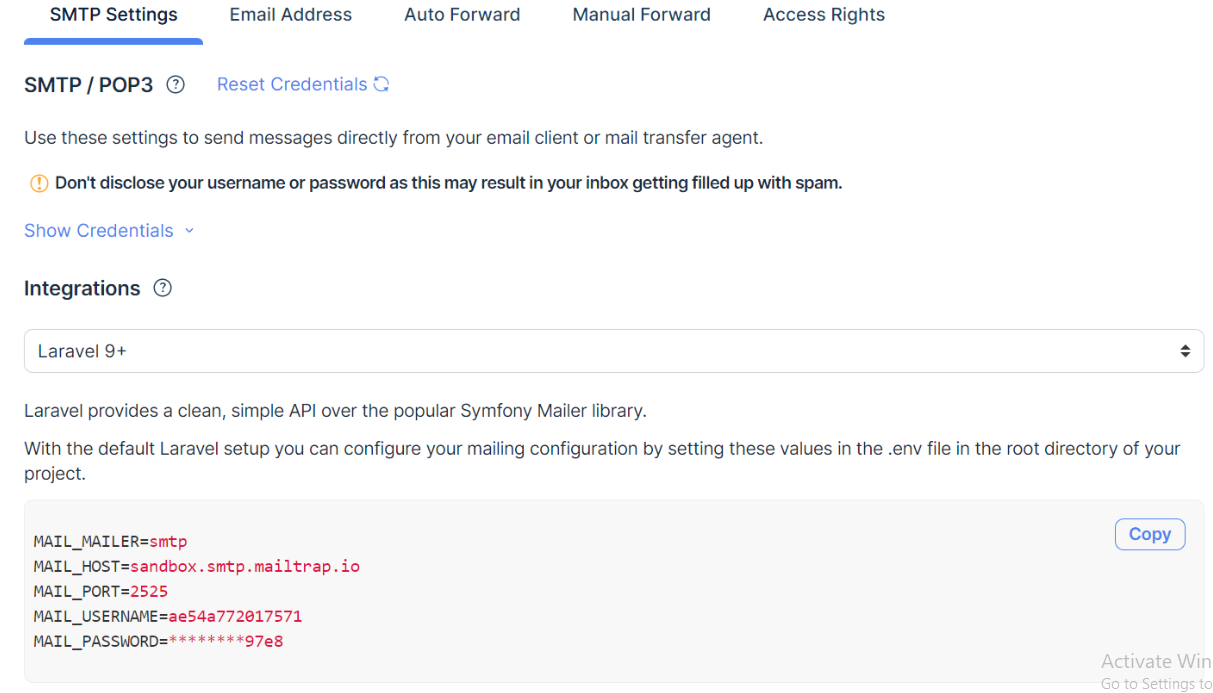
This specialized tool is designed to interact with Laravel applications’ email functionality, validating SMTP configurations and testing email addresses. It works by exploiting Laravel’s built-in mail features and common configuration patterns to determine valid credentials and email addresses without triggering standard security alerts. While developers might use similar tools for legitimate testing purposes, attackers typically employ this software to map out valid user accounts, test stolen credentials, and identify misconfigured systems that can be exploited for spam or phishing operations. The tool’s effectiveness stems from its in-depth understanding of Laravel’s architecture and its ability to simulate legitimate application traffic.
Key Features
| Feature | Description |
| Laravel-specific detection | Identifies Laravel applications and analyzes their mail configuration |
| SMTP credential testing | Tests various SMTP authentication combinations against Laravel mail systems |
| Email validation | Verifies email addresses through Laravel’s mail sending functionality |
| API exploitation | Leverages Laravel’s API endpoints related to email functionality |
| Proxy support | Rotates IP addresses to avoid detection and rate limiting |
| Config analysis | Extracts and tests SMTP configurations from exposed Laravel files |
| Error-based enumeration | Uses error messages to identify valid accounts and configurations |
How Laravel SMTP Checker 2025 Works
- Target Identification and Analysis
- Scans for Laravel applications using framework fingerprints (cookie patterns, default routes)
- Checks for exposed configuration files or environment variables (.env)
- Identifies active mail-related routes and API endpoints
- SMTP Configuration Testing
- Tests common SMTP credential combinations (mailgun, sendgrid, AWS SES)
- Attempts to extract SMTP details from exposed debug information
- Uses Laravel’s built-in mail test functionality to verify working configurations
- Email Address Validation
- Exploits password reset functionality to test email validity
- Analyzes response times and error messages to identify registered accounts
- Uses contact forms and newsletter subscriptions to verify addresses
- Tests for API endpoints that process email addresses without proper validation
- Advanced Exploitation Techniques
- Attempts mail header injection through vulnerable contact forms
- Tests for stored XSS in email template rendering
- Exploits mail log viewing functionality if present
- Attempts to escalate privileges through password reset flaws
- Payload Delivery
- For validated email addresses:
- Builds targeted phishing lists
- Prepares for credential stuffing attacks
- For compromised SMTP configurations:
- Sets up unauthorized mail sending
- Configures email forwarding rules
- Deploys backdoors through malicious email templates
- Evasion Techniques
- Mimics legitimate browser traffic patterns
- Uses progressive testing to stay below rate limits
- Leverages legitimate API endpoints to avoid WAF detection
- Randomizes user agents and request timing


