Link Exploit 2024
In the constantly evolving digital landscape, effective link management is vital for cybersecurity professionals, ethical hackers, and IT specialists. Link Exploit 2024 stands out as an advanced tool designed to analyze, manipulate, and secure URLs with high accuracy. Ideal for penetration testing, vulnerability assessments, and red team operations, this tool offers a comprehensive framework for safely testing and exploiting link-based threats.

What is Link Exploit 2024?
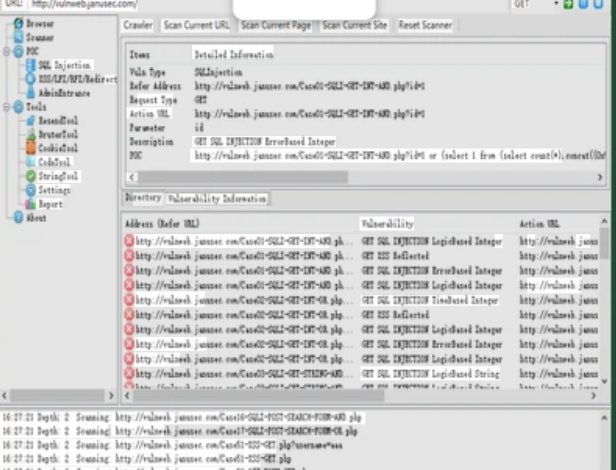
Link Exploit is a sophisticated cybersecurity application built to detect, manipulate, and exploit vulnerabilities within hyperlinks. It assists security researchers in identifying malicious link behavior, phishing threats, and URL-based attack vectors. By simulating real-world exploitation scenarios, it helps organizations strengthen their defenses against threats originating from compromised or deceptive URLs.
Detailed Features of Link Exploit 2024
| Feature | Description |
|---|---|
| Automated Link Scanning | Instantly detects malicious URLs, redirects, and hidden phishing attempts in real-time. |
| Exploit Payload Injection | Injects custom payloads into URLs to test security weaknesses and vulnerabilities. |
| Phishing Simulation | Emulates phishing attacks to assess an organization’s vulnerability to social engineering. |
| Deep Link Analysis | Analyzes URL structures, query parameters, and obfuscation methods used in cyberattacks. |
| Customizable Exploit Templates | Provides pre-built and user-defined templates for rapid vulnerability testing. |
| Stealth Mode Operation | Performs tests discreetly without triggering typical security alerts—perfect for red-team tasks. |
| Comprehensive Reporting | Generates detailed logs, risk assessments, and actionable remediation recommendations. |
| API Integration | Easily integrates with other cybersecurity tools for automated and streamlined workflows. |
Why Use Link Exploit 2024?
As cyber threats become more advanced, standard security tools often miss critical link-based vulnerabilities. Link Exploit 2024 enables security teams to proactively discover and mitigate these risks before attackers do. It is especially useful for:
Penetration Testers: Identify hidden link vulnerabilities within web applications.
SOC Teams: Improve threat detection and incident response related to URL-based attacks.
Ethical Hackers: Conduct controlled exploitation of suspicious links to improve security posture.
IT Administrators: Enforce stronger security policies to guard against malicious hyperlinks.