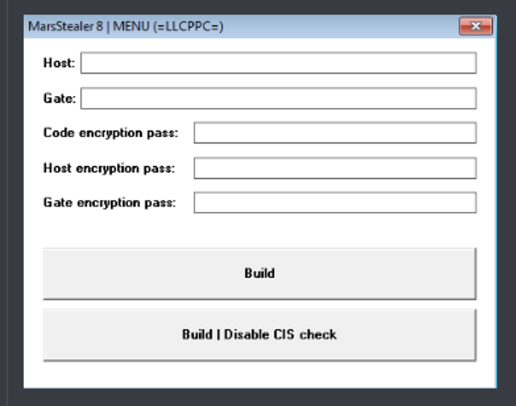
Mars Stealer v8
In the ever-evolving landscape of cybercrime, information-stealing malware has become increasingly sophisticated, with modern variants posing significant threats to individuals and organizations alike. These advanced threats specialize in covert data collection, credential harvesting, and financial fraud, often operating undetected for extended periods. The latest generation of these malicious tools demonstrates concerning improvements in evasion techniques, cross-platform compatibility, and integration with underground criminal ecosystems. Mars Stealer v8 ability to bypass traditional security measures and exfiltrate sensitive data makes them particularly dangerous in an era where digital credentials grant access to both financial assets and critical infrastructure.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This category of malware represents a specialized tool designed to systematically identify, collect, and exfiltrate valuable information from compromised systems. Unlike ransomware that announces its presence, these stealers operate silently in the background, focusing on harvesting credentials, financial data, and authentication tokens. Cybercriminals typically deploy them through phishing campaigns, malicious downloads, or exploit kits, often as part of a broader attack chain. The stolen data frequently appears on dark web marketplaces within hours of collection, where it’s purchased by other criminals for various fraudulent activities, creating a thriving underground economy around compromised credentials.

Key Features
| Feature | Description |
| Credential Harvesting | Extracts saved logins from browsers and password managers |
| Session Cookie Theft | Steals authentication tokens for session hijacking |
| Cryptocurrency Targeting | Identifies and exfiltrates wallet credentials and seed phrases |
| Form Grabbing | Captures data entered into web forms in real-time |
| Screenshot Capability | Periodically captures screen content for additional intelligence |
| File Scanning | Searches for specific document types containing valuable information |
| Anti-Analysis Techniques | Detects and evades sandboxes and security tools |
| Modular Architecture | Allows customization with additional plugins for specific targets |
How Mars Stealer v8 Works
The stealer operates through a carefully orchestrated sequence of activities:
Initial Infection
- Delivery Methods
- Malicious email attachments disguised as invoices or documents
- Compromised software installers from unofficial sources
- Exploit kits targeting unpatched browser vulnerabilities
- Execution and Persistence
- Uses process hollowing to inject into legitimate system processes
- Creates scheduled tasks or registry entries for persistence
- Disables security software through carefully timed operations


