Mercurial Grabber 2025
The cybersecurity landscape in 2025 has witnessed the emergence of highly sophisticated credential-stealing malware designed to bypass modern security measures with unprecedented efficiency. Among these threats, a particularly agile and evasive strain has gained prominence for its ability to rapidly adapt to different environments and extract sensitive authentication data. Mercurial Grabber 2025 exemplifies the growing trend of “hit-and-run” cyberattacks, where threat actors prioritize speed and stealth to harvest credentials before detection occurs. Its modular architecture and cloud-based command structure make it especially dangerous in an era where traditional perimeter defenses are increasingly insufficient against determined attackers.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This credential-stealing malware is a lightweight but powerful tool specifically engineered to harvest authentication data from compromised systems while avoiding detection. It primarily targets browser-stored credentials, session cookies, and authentication tokens that can provide access to corporate networks, cloud services, and financial accounts. Distributed through sophisticated phishing campaigns, malvertising, and supply chain compromises, it’s frequently used in business email compromise (BEC) schemes, corporate espionage, and as an initial access broker for ransomware operations. The malware’s ability to selectively target high-value credentials while maintaining a minimal footprint sets it apart from conventional information stealers.

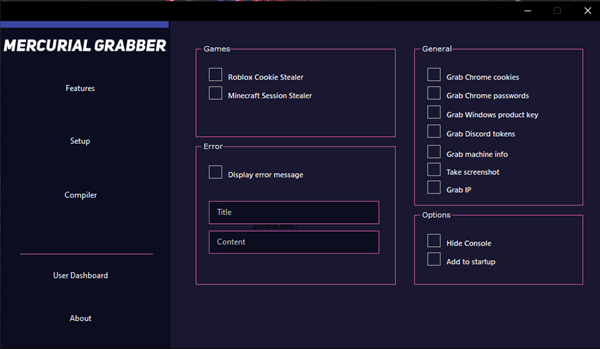
Key Features
| Feature | Description |
| Targeted Credential Harvesting | Focuses on high-value corporate and cloud service credentials |
| Session Token Theft | Extracts active authentication tokens to bypass MFA |
| Cloud API Integration | Interfaces directly with cloud provider APIs for enhanced data access |
| Memory-Resident Operation | Operates primarily in memory to avoid disk-based detection |
| Selective Exfiltration | Filters and prioritizes high-value credentials before transmission |
| Dynamic Code Loading | Downloads additional modules post-infection as needed |
| Traffic Obfuscation | Masks exfiltration as legitimate cloud service traffic |
| Auto-Cleanup | Removes forensic artifacts after successful data extraction |
How Mercurial Grabber 2025 Works
Initial Infection and Execution
The malware employs multiple advanced delivery mechanisms:
- Polymorphic JavaScript Loaders: Unique, obfuscated scripts for each infection
- Cloud Storage Abuse: Leverages legitimate cloud services for payload hosting
- Living-off-the-Land: Uses trusted system utilities like PowerShell for execution
Upon activation, the malware:
- Performs Lightweight Reconnaissance: Quickly profiles the system environment
- Establishes Temporary Persistence: Uses memory injection rather than disk-based methods
- Verifies Target Value: Checks for corporate network connections or valuable accounts
Core Credential Harvesting Process
The malware executes a rapid, targeted collection sequence:
- Browser Memory Scraping:
- Extracts active session cookies from browser processes
- Targets specific domains (Office 365, AWS, Salesforce, etc.)
- Prioritizes authentication tokens with remaining validity
- Credential Vault Extraction:
- Accesses browser password managers through memory injection
- Decrypts stored credentials using hooked API calls
- Filters results for corporate email patterns
- Cloud Service Targeting:
- Identifies installed cloud authentication clients
- Extracts cached credentials and configuration files
- Harvests API keys from development environments
Advanced Evasion Techniques
The malware incorporates innovative anti-detection methods:
- API Hook Concealment: Masks its memory hooks from security products
- Process Doppelgänging: Uses transactional NTFS to hide malicious operations
- Time-constrained Operation: Completes its mission within minutes of infection
- Cloud-based Obfuscation: Routes traffic through legitimate SaaS platforms
Data Processing and Exfiltration
The stolen data undergoes efficient processing:
- Immediate Prioritization: Sorts credentials by perceived value
- Lightweight Encryption: Uses stream ciphers for rapid protection
- Chunked Transmission: Splits data into cloud-storage-friendly packets
- Multiple Exfiltration Paths:
- Primary: Disguised as OneDrive/Dropbox sync traffic
- Secondary: Encrypted WebSocket connections
- Fallback: DNS tunneling through trusted domains
Self-Termination and Cleanup
After successful exfiltration:
- Memory Wiping: Overwrites its memory footprints
- Artifact Removal: Deletes temporary files and registry entries
- Deactivation: Kills its processes without a trace


