Miner CPUGPU Builder v1.0.1
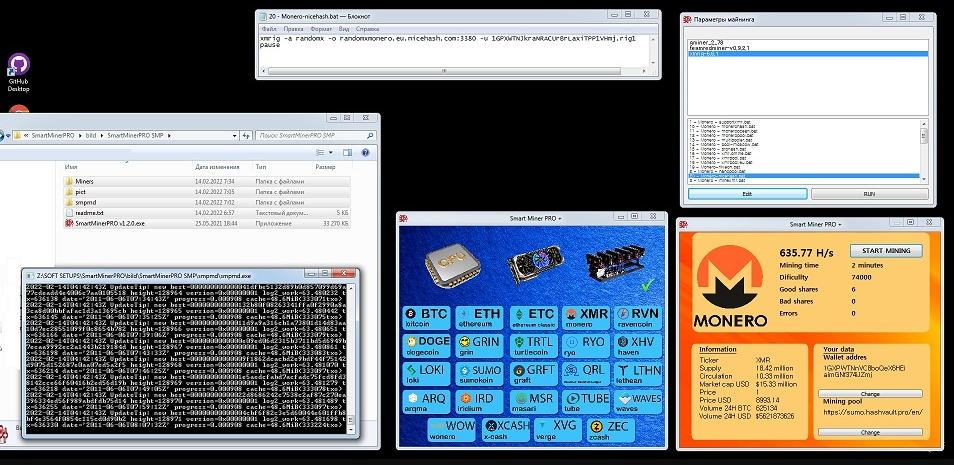
In the evolving landscape of cyber threats, malicious tools designed to exploit system resources have become increasingly sophisticated. One such tool, a cryptojacking utility, leverages a combination of CPU and GPU processing power to mine cryptocurrencies without the victim’s knowledge. These tools are often deployed silently as part of larger malware campaigns, enabling attackers to generate revenue while remaining undetected. Miner CPUGPU Builder v1.0.1 modular design allows for customization, making them adaptable to different environments and evasion techniques.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software is a cryptojacking tool that hijacks a system’s computational resources to mine cryptocurrency. It is typically distributed through phishing emails, malicious downloads, or bundled with pirated software. Once installed, it operates stealthily in the background, maximizing hardware usage to mine for an attacker’s benefit. The tool supports multiple mining algorithms and can dynamically switch between them based on hardware compatibility or to evade detection.

Key Features
| Feature | Description |
| Multi-algorithm support | Works with various mining algorithms (e.g., XMRig for CPU, Ethminer for GPU). |
| Persistence mechanisms | Ensures continuous operation via registry edits, scheduled tasks, or services. |
| Evasion techniques | Uses process hollowing, obfuscation, and traffic masking to avoid detection. |
| Dynamic configuration | Remote updates of mining pools and wallets via C2 servers. |
| Resource throttling | Adjusts CPU/GPU usage to avoid suspicion while maintaining profitability. |
How Miner CPUGPU Builder v1.0.1 Works
Infection and Deployment
The software is typically delivered through social engineering or exploit kits. Once executed, it deploys a dropper that extracts and installs the mining payload. The installer may also disable security software or manipulate system settings to maintain persistence.
Payload Execution
The core component consists of a miner configured to connect to a remote mining pool. It uses the victim’s hardware to solve cryptographic puzzles, earning cryptocurrency for the attacker. The miner operates in a hidden process, often injected into a legitimate system application (e.g., svchost.exe) to evade process-based detection.
Evasion and Persistence
To avoid detection, the tool employs several techniques:
- Process Hollowing: Replaces the memory space of a legitimate process with malicious code.
- Traffic Obfuscation: Encrypts communication with mining pools to blend in with normal traffic.
- Resource Management: Limits CPU/GPU usage to prevent noticeable system slowdowns.
Persistence is maintained through methods like creating scheduled tasks, modifying registry keys, or installing a service. Some variants also include watchdog processes to restart the miner if it crashes or is terminated.
Payload Delivery
The miner communicates with a command-and-control (C2) server to receive updates, such as new wallet addresses or mining pool configurations. This allows attackers to switch strategies without redistributing the malware. In some cases, the software may also download additional payloads, turning the infected system into part of a botnet.


