Mini Mail Viewer 2.0
Email remains one of the most targeted attack vectors in cybersecurity, with threat actors constantly developing tools to exploit email clients and protocols. In 2024, specialised email monitoring utilities have been repurposed by malicious actors to facilitate unauthorised access to sensitive communications. Mini Mail Viewer 2.0 tools pose a significant threat to both individual privacy and organizational security, as they can silently intercept, monitor, and exfiltrate email content without the user’s knowledge. Their role in modern cyberattacks has expanded from simple espionage to supporting business email compromise (BEC), credential harvesting, and targeted phishing campaigns. The lightweight nature and apparent legitimacy of these tools make them particularly dangerous, as they often evade traditional security detection while providing attackers with persistent access to email accounts.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
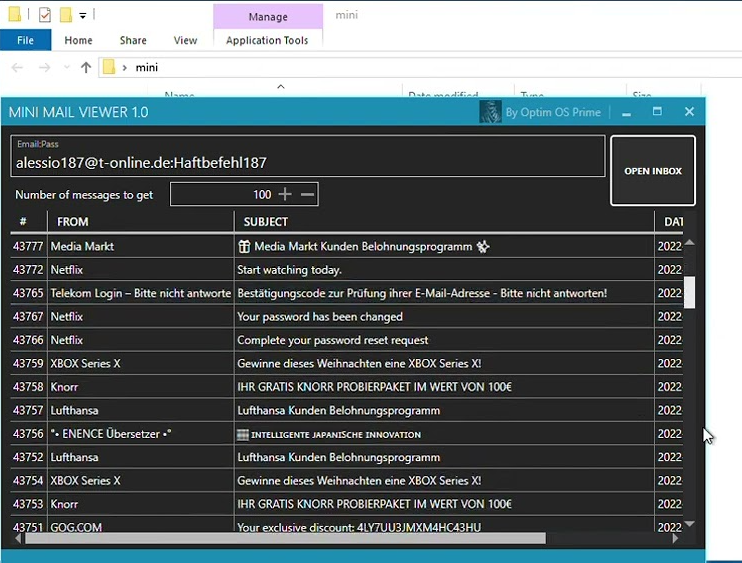
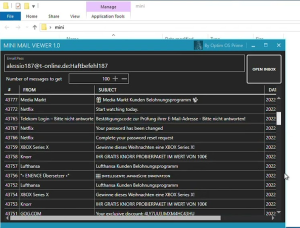
This email monitoring tool is designed to silently access and archive email content from various mail clients and protocols. While marketed as a productivity utility for email management, its functionality makes it particularly useful for malicious actors seeking to monitor email accounts without authorization. The software operates by establishing persistent connections to email servers, downloading messages in the background, and storing them in an organized database. Attackers typically deploy this tool after gaining initial access to a system, using it to maintain long-term surveillance of email communications, harvest sensitive information, and identify high-value targets for further exploitation. Its “lite” version is specifically designed to be less detectable by security software while retaining core monitoring capabilities.
Key Features
| Feature | Description |
| Multi-protocol Support | Works with POP3, IMAP, SMTP, and Exchange protocols |
| Stealth Mode Operation | Runs with minimal system footprint and avoids common detection vectors |
| Email Content Extraction | Retrieves full messages including attachments and metadata |
| Search and Filtering | Advanced filtering for sensitive keywords and sender patterns |
| Automated Archiving | Stores emails in encrypted local databases for later exfiltration |
| Persistent Connection | Maintains constant access to email accounts without triggering security alerts |
| Remote Access Module | Optional component for external control and data retrieval |
How Mini Mail Viewer 2.0 Works
- Initial Setup and Configuration
- Accepts email account credentials through:
- Manual input
- Configuration file import
- Credential harvesting from system memory
- Configures connection parameters:
- Server addresses and ports
- Sync intervals
- Download preferences (headers only/full messages)
- Sets up local encrypted storage database
- Protocol-Specific Connection
- For IMAP accounts:
- Creates hidden folder for message storage
- Uses IDLE command for real-time monitoring
- Avoids marking messages as read
- For POP3 accounts:
- Configures leave-on-server option
- Uses APOP authentication when available
- For Exchange/ActiveSync:
- Mimics mobile device sync patterns
- Uses minimal sync requests to reduce traffic
- Message Processing
- Downloads email content in stages:
- Headers only for initial scan
- Full content for flagged messages
- Attachments as separate files
- Analyzes message content for:
- Sensitive keywords (password, invoice, confidential)
- Financial information
- Attachment types
- Maintains local message database with:
- Full-text search capability
- Tagging system
- Relationship mapping
- Stealth and Evasion Techniques
- Network traffic blending:
- Mimics standard email client patterns
- Randomizes sync intervals
- Uses TLS encryption like legitimate clients
- Process hiding:
- Uses legitimate-sounding process names
- Implements process hollowing techniques
- Leverages trusted publisher certificates
- Storage obfuscation:
- Encrypted local database
- Hidden system folders
- File naming conventions matching system files
- Data Exfiltration
- Multiple export options:
- Compressed archives via email
- Cloud storage uploads
- Direct transfer to C2 servers
- Optional modules for:
- Real-time forwarding of selected messages
- Automated replies to intercept conversations
- Attachment modification
- Persistence Mechanisms
- Installation as:
- Browser extension (for webmail)
- System service
- Scheduled task
- Self-preservation features:
- Automatic updates
- Process monitoring and restart
- Detection avoidance


