MVII Port Scanner v1.0
Port scanning is a fundamental technique in network reconnaissance, often employed to identify open ports and services on target systems. One such tool, MVII Port Scanner v1.0, is capable of scanning a predefined range of ports (typically 1-65535) to detect vulnerabilities in networked devices. While port scanners are legitimate tools for network administrators, they are also frequently leveraged in cyberattacks to map attack surfaces, identify weak points, and facilitate subsequent exploitation. In the wrong hands, such tools can be used to launch targeted attacks, including brute-force attempts, service exploitation, or malware deployment.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software is a lightweight yet powerful port scanner designed to quickly and efficiently identify active ports and services on a target system. It is commonly used by penetration testers, security researchers, and network administrators to assess network security, troubleshoot connectivity issues, or audit firewall rules. However, malicious actors may also use it to gather intelligence before launching attacks. The tool supports various scanning techniques, including TCP SYN, UDP, and version detection, making it versatile for different scenarios.
Key Features of MVII Port Scanner v1.0
| Feature | Description |
|---|---|
| TCP SYN Scan | A stealthy scan that avoids a full TCP handshake, reducing detection risk. |
| UDP Scan | Identifies open UDP ports, which are often overlooked but vulnerable. |
| Version Detection | Probe services to determine their version, aiding in vulnerability analysis. |
| Custom Range Scan | Allows users to specify port ranges for targeted scanning. |
| Fast & Efficient | Optimized for speed, capable of scanning large networks quickly. |
| Output Logging | Saves results in multiple formats for further analysis and review. |
How It Works
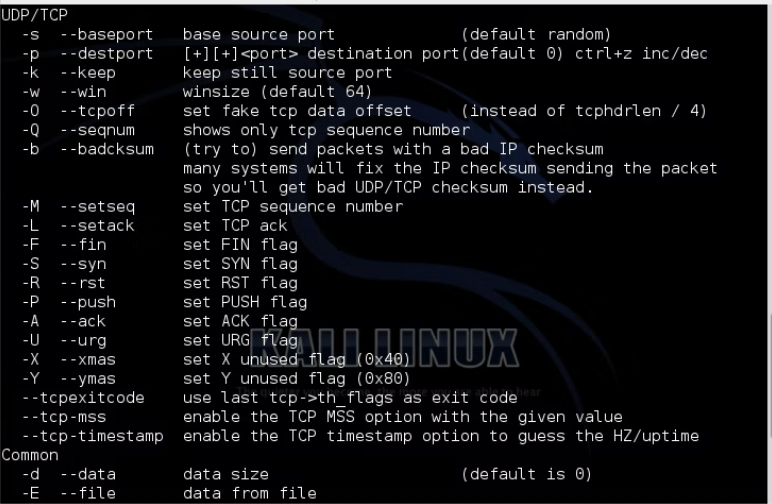
Scanning Techniques
The software employs several techniques to identify open ports and services:
TCP SYN Scan (Half-Open Scan):
Instead of completing a full TCP three-way handshake, the scanner sends a SYN packet to the target port.
If the target responds with a SYN-ACK, the port is open; if it sends an RST, the port is closed.
This method is stealthier than a full connection, as it doesn’t establish a full connection.
UDP Scan:
UDP ports are scanned by sending UDP packets to each target port.
If the port responds with an ICMP “port unreachable” message, it is closed. A lack of response may indicate an open port.
UDP scanning is slower and less reliable than TCP due to the connectionless nature of UDP.
Version Detection:
After identifying an open port, the scanner probes the service running on it to determine its version.
This is done by analyzing banners or responses from the service, which can reveal vulnerabilities.
Functionality
The tool first retargets the target’s hostname to an IP address, if necessary.
It then iterates through the specified port range, sending probes based on the selected scan type.
Responses are analyzed to determine port status (open, closed, filtered).
Results are compiled into a report, highlighting potential vulnerabilities.
Payload Delivery (Malicious Use Case)
In cyberattacks, the scanner may be used to:
Identify exploitable services, such as outdated FTP or SSH servers.
Map network topology for lateral movement.
Serve as a precursor to delivering malware (e.g., by targeting vulnerable RDP or SMB ports).
The scanner itself does not deliver payloads but provides critical intelligence for subsequent stages of the attack.