Neos Email Spoofer 2024
In the ever-evolving landscape of cybersecurity, tools like Neos Email Spoofer 2024 play a critical role in helping professionals test vulnerabilities, educate users, and strengthen email security. This powerful software allows users to simulate email spoofing attacks ethically, making it an essential asset for penetration testers, IT administrators, and cybersecurity trainers.
What Is Neos Email Spoofer 2024?
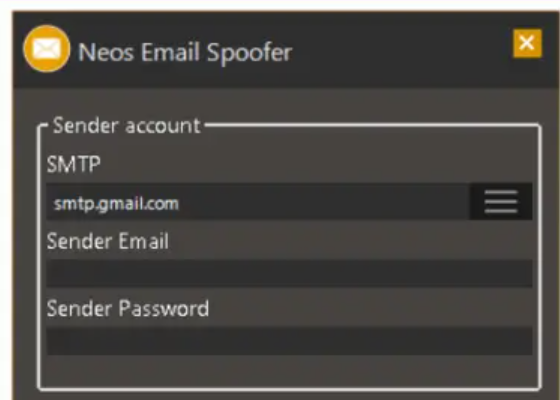
Neos Email Spoofer is an advanced email spoofing tool designed for legitimate security testing and research purposes. It enables users to send emails that appear to come from any address, domain, or sender name, mimicking the techniques used by malicious actors. Unlike illegal spoofing tools, Neos is built for ethical hacking, helping organizations identify weaknesses in their email systems and train employees to recognize phishing attempts.
Detailed Features
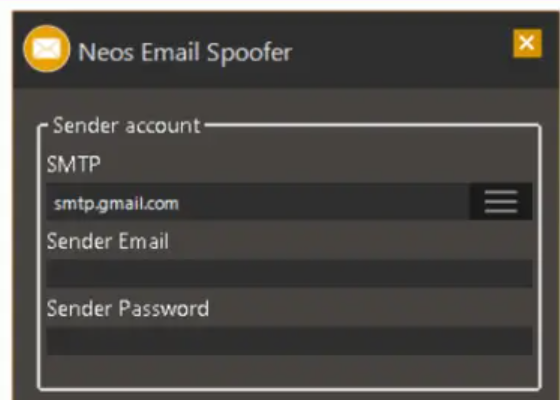
- Customizable Email Headers – Modify sender names, email addresses, and domains to simulate real-world phishing scenarios.
- SMTP Server Integration – Connect to external SMTP servers or use built-in proxies for seamless email delivery.
- HTML & Attachment Support – Craft sophisticated phishing templates with embedded HTML, images, and malicious-looking attachments (for analysis only).
- IP & Geolocation Masking – Spoof originating IP addresses and geolocation data to test email filters.
- Encrypted Logs & Sessions – Maintain secure, encrypted logs of all spoofed emails for auditing and reporting.
- Multi-Platform Compatibility – Works on Windows, Linux, and macOS, with CLI and GUI options.
- Real-Time Analytics – Track open rates, click-through rates, and user interactions to assess vulnerability.
- Anti-Detection Bypass – Test against SPF, DKIM, and DMARC protocols to evaluate email security effectiveness.
Why Use Neos Email Spoofer 2024?
Email spoofing remains one of the top attack vectors for cybercriminals. By using Neos Email Spoofer 2024 ethically, organizations can:
- Identify Security Gaps – Discover flaws in email authentication protocols.
- Train Employees – Conduct realistic phishing simulations to improve awareness.
- Comply with Security Standards – Meet regulatory requirements for cybersecurity testing.
- Enhance Incident Response – Prepare IT teams to detect and mitigate spoofing attacks.