Nimrod Stealer 2025
Cyber threats continue to evolve, with information-stealing malware playing a significant role in modern attacks. One such example is a sophisticated stealer that emerged in recent years, capable of extracting sensitive data from infected systems while evading detection. Nimrod Stealer 2025 of malware is often distributed through phishing campaigns, malicious downloads, or exploit kits, targeting both individuals and organizations. Once deployed, it can harvest credentials, financial data, and other valuable information, which is then sent to a command-and-control (C2) server for exploitation. Its modular design and anti-analysis techniques make it a persistent threat in the cybersecurity landscape.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
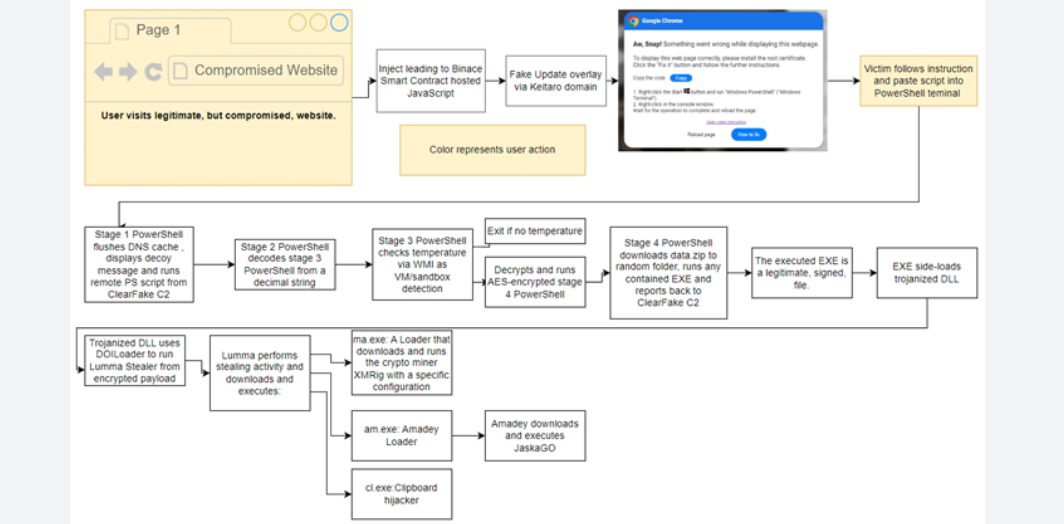
This malware is a type of information stealer designed to collect and exfiltrate sensitive data from compromised systems. It primarily targets web browsers, cryptocurrency wallets, FTP clients, and other applications storing login credentials or financial information. Cybercriminals typically use it to steal personal and corporate data, which is then sold on underground forums or used in further attacks, such as identity theft, financial fraud, or ransomware deployment. Its flexibility allows it to be distributed as a standalone executable or embedded within other malicious payloads.

Key Features of Nimrod Stealer 2025
| Feature | Description |
| Credential Harvesting | Extracts saved passwords, cookies, and autofill data from browsers. |
| Cryptocurrency Theft | Targets wallet files and clipboard data to hijack crypto transactions. |
| System Reconnaissance | Collects system details (OS, hardware, and installed software) for profiling purposes. |
| Anti-Detection | Uses obfuscation, packing, and sandbox evasion to avoid analysis. |
| C2 Communication | Sends stolen data to a remote server via encrypted channels. |
| Persistence | Establishes registry modifications or scheduled tasks to maintain access. |
| Modular Plugins | Supports add-ons for expanded functionality, such as keylogging and screen capture. |
How Nimrod Stealer 2025 Works
Infection and Delivery
The malware is typically delivered through social engineering tactics, such as phishing emails with malicious attachments or fake software updates. Alternatively, it may be bundled with pirated software or distributed via exploit kits targeting vulnerabilities in outdated applications. Once executed, it deploys its payload while employing techniques such as process hollowing or DLL injection to evade detection.
Data Collection Techniques
After gaining a foothold, the malware scans the system for target applications, including web browsers (Chrome, Firefox, Edge), email clients, and cryptocurrency wallets. It accesses browser databases, such as SQLite files storing login credentials, and decrypts them using built-in methods. Additionally, it may monitor the clipboard for cryptocurrency addresses and replace them with attacker-controlled ones, a technique known as “clipboard hijacking.”
Evasion and Persistence of Nimrod Stealer 2025
To avoid detection, the malware employs code obfuscation, anti-debugging tricks, and checks for virtualized environments (e.g., VirtualBox, VMware). If it detects analysis tools, it may terminate execution or alter its behavior. For persistence, it may create scheduled tasks, modify registry keys, or inject itself into legitimate processes.
Data Exfiltration
Stolen data is compressed, encrypted, and transmitted to a C2 server via HTTPS or other covert channels. Some variants use decentralized storage (e.g., Telegram bots or blockchain-based storage) to obscure communication. Attackers then aggregate the data for exploitation or sale.
Post-Exploitation
In some cases, the malware may download additional payloads, such as ransomware or remote access trojans (RATs), turning a simple data theft operation into a more severe breach.
By combining stealth, efficiency, and adaptability, this type of malware remains a significant threat, requiring proactive defense measures such as endpoint detection, regular software updates, and user education to mitigate risks.


