njRAT ACS Version 2024 Cracked
NjRAT ACS Version 2024 represents the latest iteration of a notorious remote access trojan that has become a staple in cybercriminal operations. This enhanced version continues the legacy of its predecessors while incorporating advanced evasion techniques and expanded functionality, making it particularly dangerous in the current threat landscape. Security researchers have observed its widespread use in financial fraud, data theft, and botnet operations, with attackers leveraging its modular design to adapt to various malicious campaigns. The 2024 variant demonstrates concerning improvements in persistence mechanisms and anti-analysis capabilities, cementing its position as a go-to tool for both novice hackers and organized cybercrime groups.
Download Link 1
Download Link 2
Download Link 3

What is the NJRAT ACS Version 2024
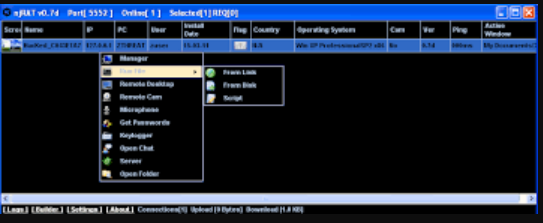
NjRAT ACS Version 2024 is a sophisticated remote administration tool repurposed for malicious activities, offering attackers complete control over compromised systems. Its user-friendly interface and extensive feature set make it particularly appealing to cybercriminals with varying skill levels. The software is primarily distributed through phishing campaigns, malicious downloads, and exploit kits, often disguised as legitimate software or documents. Once installed, it enables attackers to:
- Steal sensitive information (credentials, financial data, personal files)
- Execute remote commands (full system control via command line)
- Deploy additional payloads (ransomware, cryptocurrency miners)
- Conduct surveillance (webcam access, microphone recording)
- Build botnets (for coordinated attacks or spam distribution)
Key Features
| Feature | Description |
| Remote Desktop Control | Provides real-time access to the victim’s screen and input devices. |
| Keylogging | Captures keystrokes to harvest passwords, messages, and other sensitive data. |
| File Management | Allows attackers to browse, upload, download, and modify files on the system. |
| Process Manipulation | Enables termination or creation of system processes. |
| Persistent Access | Maintains long-term control via registry modifications and hidden startup entries. |
| Data Exfiltration | Sends stolen information to attacker-controlled servers via encrypted channels. |
| Evasion Techniques | Uses code obfuscation, process injection, and anti-sandbox measures. |
How NjRAT ACS Version 2024 works
1. Delivery and Initial Compromise
The malware typically spreads through:
- Phishing emails with malicious attachments (e.g., fake invoices, resumes).
- Compromised websites host drive-by downloads.
- Trojanized software (cracked applications or fake updates).
Upon execution, NjRAT ACS Version 2024:
- Drops payloads in hidden directories.
- Modifies registry keys to ensure automatic startup.
- Disables security tools (e.g., Windows Defender, firewalls).
2. Command and Control (C2) Communication
The malware establishes a connection to the attacker’s server using:
- Encrypted HTTP/HTTPS requests (blending with normal traffic).
- Dynamic DNS or bulletproof hosting to evade takedowns.
- Fallback mechanisms (multiple backup C2 servers).
Once connected, the attacker can:
- Issue remote commands (e.g., execute scripts, disable processes).
- Update the malware (download new modules or configurations).
3. Post-Infection Activities
Attackers leverage NjRAT ACS Version 2024 to:
- Harvest credentials from browsers, email clients, and FTP software.
- Capture screenshots and record keystrokes for espionage.
- Deploy ransomware or cryptocurrency miners for financial gain.
- Use the victim’s system as a proxy for further attacks.
4. Evasion and Persistence
To avoid detection, the malware employs:
- Process hollowing (injects into legitimate processes like explorer.exe).
- Code obfuscation (encrypts strings and API calls).
- Sandbox detection (checks for virtualized environments).
- Regular updates (fetches new evasion techniques from C2).


