njRAT v0.8.0 LIME EDITION
The cyber threat landscape continues to evolve with the resurgence of modified legacy Remote Access Trojans (RATs) that have been enhanced with modern capabilities. Among these, a particularly concerning variant has emerged, combining the proven effectiveness of traditional RAT functionality with contemporary evasion techniques. njRAT v0.8.0 exemplifies how threat actors are revitalizing older codebases with new features to bypass modern security controls while maintaining the reliability of time-tested attack vectors. Its growing prevalence in both targeted attacks and broad campaigns highlights the ongoing risk posed by these adaptable threats in an era of increasingly sophisticated cyber defenses.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
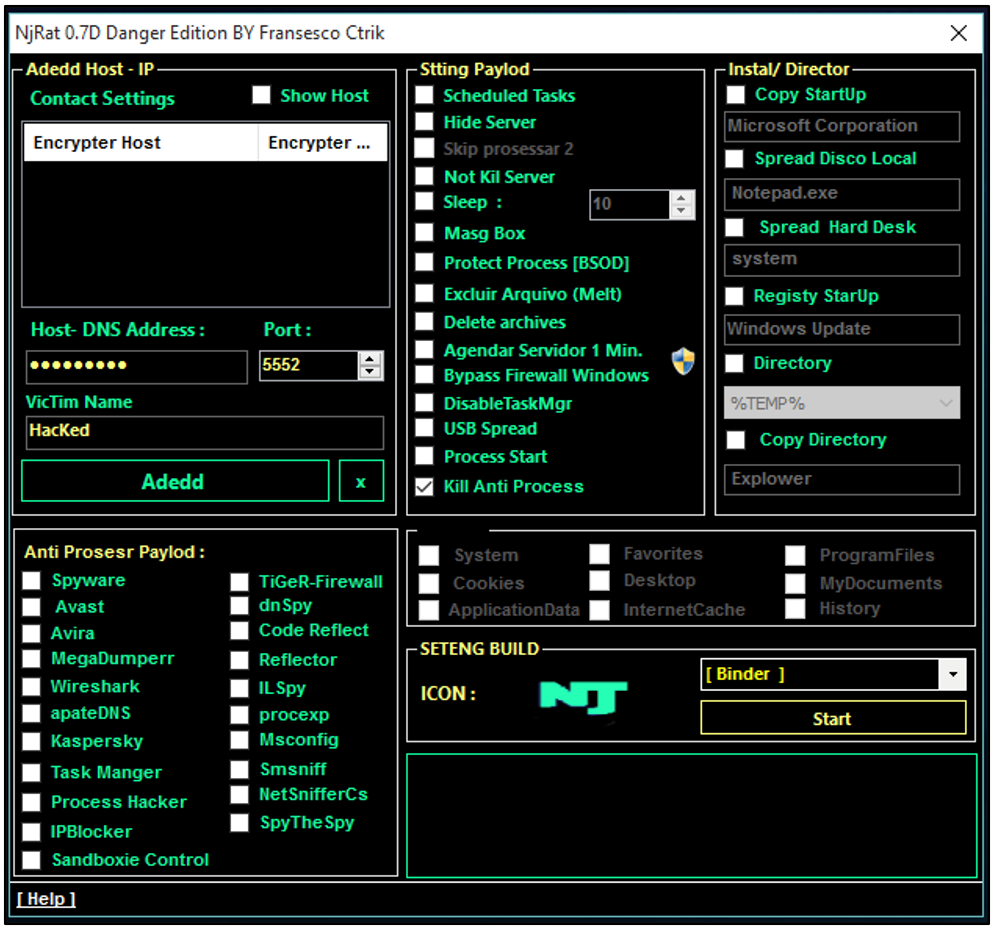
This software is an enhanced version of a well-known RAT framework that has been modified with additional capabilities and a refreshed codebase. It provides attackers with comprehensive remote control over infected systems while incorporating modern evasion techniques. Primarily distributed through phishing emails, malicious documents, and drive-by downloads, it is commonly used for credential theft, financial fraud, distributed denial-of-service (DDoS) attacks, and as a foothold for more extensive network compromises. The “Lime Edition” modifications specifically focus on improved persistence mechanisms and expanded plugin support, making it particularly versatile for various malicious operations.

Key Features
| Feature | Description |
| Remote System Control | Full GUI-based access to victim machines |
| Keylogging | Captures keystrokes including credentials and sensitive data |
| Webcam/Mic Access | Enables surreptitious audio/video recording |
| File Management | Upload, download, and execute files on victim systems |
| Process Manipulation | Start, stop, and inject code into running processes |
| DDoS Capabilities | Conducts coordinated network attacks from infected hosts |
| Plugin Architecture | Supports modular expansion for additional functionality |
| Persistence | Multiple mechanisms including registry modifications and service creation |
| Evasion Techniques | Basic anti-VM and anti-sandbox features |
How njRAT v0.8.0 Works
Infection and Initial Compromise
The malware typically spreads through:
- Weaponized Documents: Malicious Office files with embedded macros
- Exploit Kits: Leveraging known vulnerabilities in outdated software
- Social Engineering: Fake software installers or cracked applications
Upon execution, the malware:
- Drops Payload: Installs itself in the %AppData% or %Temp% directories
- Establishes Persistence: Creates registry run keys or scheduled tasks
- Connects to C2: Reaches out to command servers via HTTP or TCP
Core Functionality
Once installed, the RAT provides attackers with multiple control options:
- Remote Access Module:
- Provides live desktop viewing and control
- Supports file browsing and transfer operations
- Enables command execution via built-in terminal
- Surveillance Features:
- Keylogging captures all keyboard input
- Webcam streaming with adjustable quality settings
- Audio recording from microphone
- Network Attack Tools:
- SYN flood and UDP flood capabilities
- Botnet coordination for synchronized attacks
- System Manipulation:
- Process management and termination
- Registry editing functionality
- Screenshot capture at specified intervals
Communication and Evasion
The malware employs several techniques to maintain stealth:
- Basic Obfuscation: Simple string encryption and code packing
- C2 Communication: Uses standard HTTP requests blended with normal traffic
- Port Hopping: Can switch communication ports if blocked
- Kill Switch: Self-destruct mechanism triggered by specific commands
Payload Delivery
Additional malicious payloads can be delivered through:
- Plugin System: Modular components for expanded functionality
- Update Mechanism: Can download and execute new versions
Secondary Payloads: Delivers ransomware or other malware as needed


