Office Exploit Builder Cracked 2025
Office Exploit Builder delivery has seen a resurgence in modern cyberattacks, with threat actors increasingly leveraging weaponized Office documents as their initial infection vector. The availability of sophisticated exploit builders has significantly simplified the process of creating malicious documents that can bypass security controls. Cracked versions of these tools circulating in underground forums have lowered the barrier to entry, enabling even novice attackers to launch sophisticated campaigns. These malicious documents remain particularly effective because they exploit the inherent trust users place in common file formats, while leveraging the complex scripting capabilities built into productivity software.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
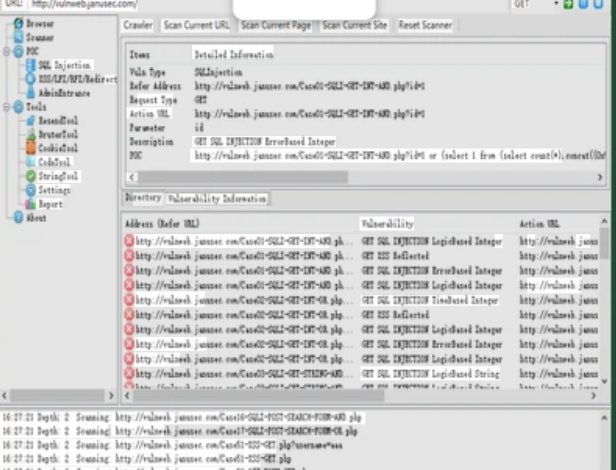
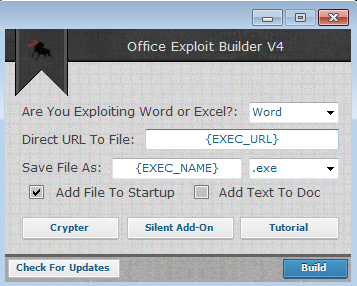
This software is a specialized toolkit designed to automate the creation of malicious Office documents containing embedded exploits and payloads. It provides a graphical interface that allows attackers to generate weaponized Word, Excel, and PowerPoint files without requiring advanced technical skills. The toolkit is typically used in phishing campaigns, targeted attacks against organizations, and malware distribution schemes. While initially developed for penetration testing, its cracked version has become popular among cybercriminals due to its ability to bypass email security gateways and exploit the widespread use of Office software in business environments.
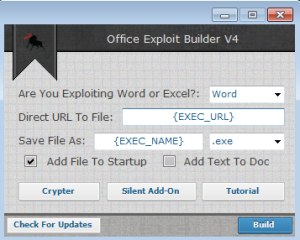
Key Features of Office Exploit Builder
| Feature | Description |
| Exploit Integration | Supports 20+ documented Office vulnerabilities |
| Payload Obfuscation | Multiple encryption and anti-sandbox techniques |
| Template Library | Pre-built malicious document templates for common scenarios |
| Macro Generator | Creates VBA scripts with evasion capabilities |
| Polyglot Files | Generates files that are valid in multiple formats |
| C2 Integration | Built-in connections to command-and-control frameworks |
| Steganography | Hooks for hiding payloads in document elements |
How Office Exploit Builder Works
The software employs a sophisticated document weaponization process:
- Exploit Selection & Configuration
- Presents a menu of available Office vulnerabilities
- Recommends exploits based on the target Office version
- Automatically generates necessary exploit components:
- Malformed OLE objects
- Corrupted document structures
- Memory corruption triggers
- Payload Integration
- Embeds the malicious payload using various techniques:
- OLE object embedding
- External relationship references
- VBA macro injection
- Implements multiple obfuscation layers:
- String encryption
- Variable scrambling
- Dead code insertion
- Evasion Techniques
- Implements document-level evasion:
- Sets convincing metadata (author, company)
- Uses authentic-looking templates
- Includes decoy content
- Incorporates runtime checks:
- Sandbox detection
- Virtual machine checks
- User interaction verification
- Delivery Mechanism
- Generates convincing email templates
- Creates password-protected archives
- Sets up malicious download sites
- Implements click tracking